More stories

The Essential Guide to Secrets Scanning
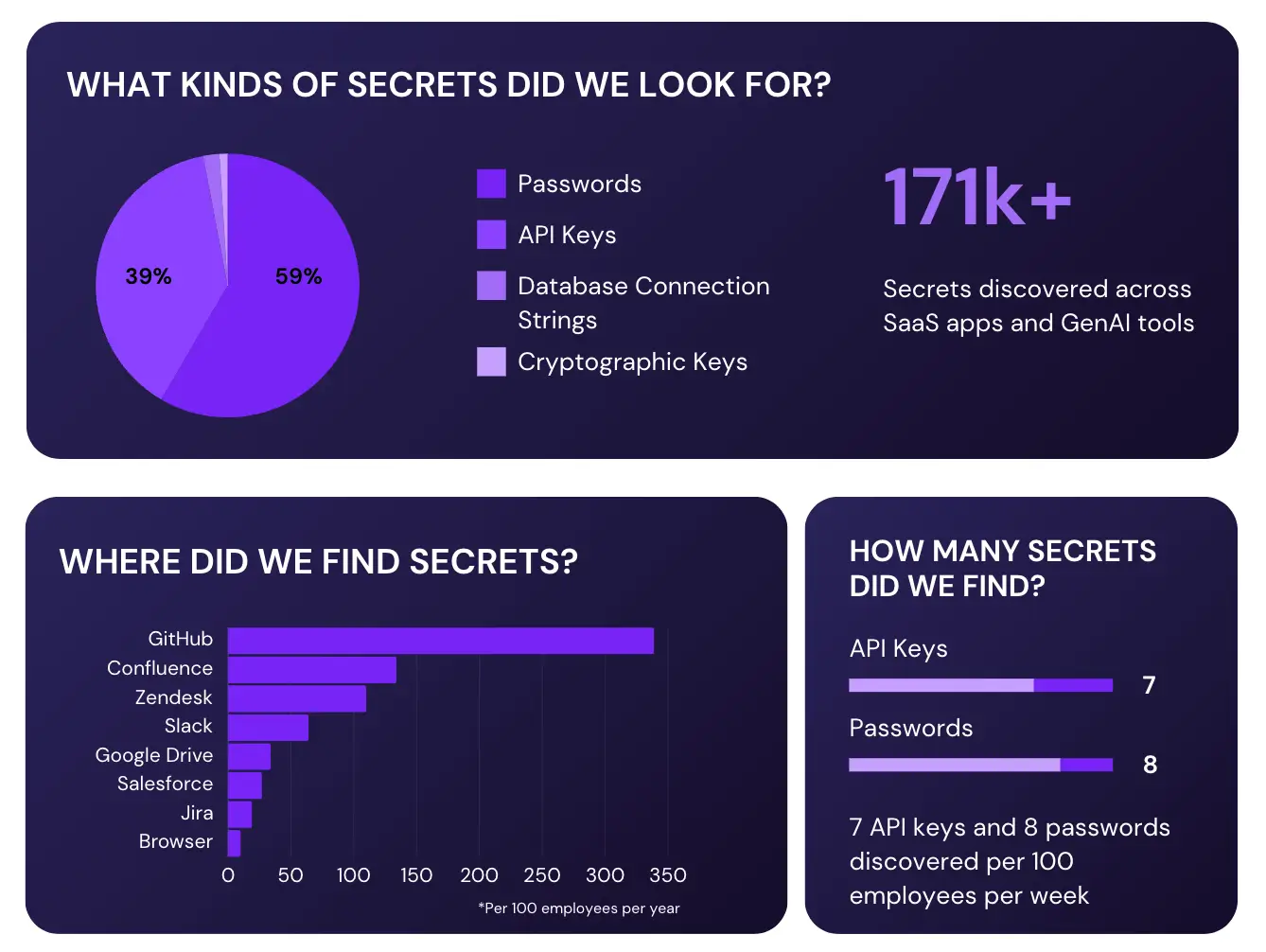
While API keys are a necessary part of modern software development, they can also be a major security risk. If an attacker is able to steal an API key, they can gain access to the data and resources that key is meant to protect. There are a number of steps you can take to protect your API keys, secrets, and credentials and prevent them from being stolen. One such method that we will cover in depth in this guide is secret scanning.

5 Stages of the Vulnerability Management Process
The threat landscape in IT is ever-evolving, with new risks arising practically daily. Trying to anticipate the next type of threat can feel a little like playing whack-a-mole. Instead, IT teams are focusing on vulnerability management: reducing the opportunities for hackers and other bad actors to find a weakness in cyber defenses.

SaaS Data Loss Prevention: What is it and Why is it Important?
With the rise of cloud-based applications, data loss prevention (DLP) has become an increasingly important part of information security. DLP refers to the policies and technologies used to prevent sensitive data from being lost or stolen. In the context of SaaS, this can include both the security measures implemented by the SaaS provider and the steps taken by the customer to protect their data. In this blog post, we'll provide a more detailed overview of what SaaS DLP is, why it's important, and how you can go about setting up a DLP strategy for your business.

Understanding Sensitive Data Discovery: Classification and Tools
In its 2022 Cost of a Data Breach report, IBM notes that for 83% of companies, it’s not if a data breach will happen — but when. The sheer volume of data, as well as the difficulty in monitoring shadow IT and the shift to remote work, means that IT security teams face a persistent and ever-changing risk landscape that makes it extremely difficult to keep information secure.

Covered Entities vs Non-Covered Entities Under HIPAA
The Health Insurance Portability and Accountability Act (HIPAA) was enacted in 1996 and sets forth a comprehensive set of standards for protecting sensitive patient health information. The Privacy Rule applies to all entities that fall within the definition of a "covered entity", which generally includes healthcare providers, health plans, and clearinghouses.

What is the FTC Safeguards Rule?
The FTC Safeguards Rule, is a set of regulations promulgated by the Federal Trade Commission in order to protect the privacy of consumers' personal information. The Rule requires financial institutions to develop, implement, and maintain a comprehensive information security program designed to safeguard customer information.

Establish an Efficient DLP Policy With These 5 Best Practices
Strong data loss prevention requires two things: a strong policy that guides user actions and permissions, and the tools to monitor and manage data security. Many organizations know they need to invest in software, platforms, and other security settings to create secure networks, endpoints, and cloud settings. But not every organization has a strong DLP policy to guide these tools.

Why Data Loss Prevention strategy is core to successful M&A
When two companies merge, there is typically a lot of data that needs to be transferred between the two organizations. This data may include confidential information such as customer records, financial reports, and employee data. If this data falls into the wrong hands, it could be used to commit fraud or theft. That's where data loss prevention (DLP) comes in.

Your Definitive Guide to Data Security Posture Management (DSPM)
With high-profile data breaches making headlines on a regular basis, it's no wonder that data security is top of mind for so many organizations. But what exactly is data security posture management (DSPM)? In this blog post, we'll take a closer look at DSPM and how it can help your business keep its data safe and secure.

The Importance of Email DLP for Remote Organizations
Email is a popular channel for hackers: phishing attacks and malware usually originate from email. In 2022, Verizon found that 82% of breaches involved the human element: phishing emails and ransomware delivered via email continue to plague organizations of all sizes.

What Is Cloud DLP And Why Do You Need It For Remote Work?
Remote work is not going away. Depending on who you ask, experts believe 35% - 65% of the US workforce will continue to work remotely, permanently. Remote work was a trend that began well before the pandemic and will continue to be the preferred way to work for companies and employees alike.

Now Available: Nightfall Expands Data Security and Compliance for Salesforce Customers
By design, Salesforce is an environment where customer PII and other sensitive information must be shared and stored. However, compliance regulations like PCI DSS, HIPAA, GDPR, CCPA, and others limit this storage and usage of customer data to only what’s justifiably required for an organization to carry out its duties.

Uber Investigating Alleged Breach of Critical SaaS and Cloud Security Systems
On Thursday evening, around 6:25 PM, Uber announced that it was responding to a cybersecurity incident. While Uber hasn’t gone into details about what happened, the purported threat actor has openly corresponded with several security professionals, including Sam Curry at Yuga Labs, Corben Leo at Zellic.io and The New York Times.

What is Data Lineage and Why Does it Matter in Data Loss Prevention?
Discover what data lineage is and why combining data lineage with AI-driven classification is critical for modern DLP strategies. Learn how tracking data's origin and movement while accurately identifying sensitive content prevents leaks in SaaS, AI, and cloud environments.

The Top 5 Cyberhaven Alternatives and Competitors in 2025
Explore the top Cyberhaven alternatives and competitors in 2025. Discover solutions like Nightfall AI, Code42 Incydr, Proofpoint ObserveIT, Endpoint Protector, and Symantec DLP to address modern data loss prevention (DLP) challenges with advanced features, seamless deployment, and comprehensive coverage.

Here’s What We Can Learn from the Cyberhaven Incident
In December 2024, Cyberhaven fell victim to a sophisticated cyberattack that exploited a phishing campaign targeting its Chrome Web Store account. This breach compromised over 400,000 users by injecting malicious code into its browser extension, exfiltrating sensitive data such as cookies and session tokens. The incident ...

Code42 Incydr: The Essential Analysis with 50+ FAQs and Top Alternatives
Code42 Incydr is among the legacy solutions aiming to mitigate insider threats, yet it doesn’t always meet every organization’s needs. In the following article, we examine Code42’s capabilities and limitations through a 60-question FAQ that addresses everything you'd want to know when evaluating DLP and IRM solutions.

Enhance Data Governance & Intelligence across SaaS Systems
Enterprise legal, compliance, and governance teams struggle to detect, manage, govern, and protect information in near real time. Similarly, litigation, HR and investigation teams struggle with data intelligence on information they have collected from cloud applications like Slack and Google Workspace.

Learn How to Protect Codebases from Secrets Exfiltration
Listen to Nightfall’s CTO, Rohan Sathe, and product specialist, Michael Osakwe, to learn about the increased exfiltration risks posed by code repositories. Learn how threat actors are incorporating targets like GitHub into their attacks, why this has become more common, and best practices to reduce your attack surface.
Discover Secrets Leaks in Code Repos with Nightfall for GitHub
Git-based repositories can create environments where secrets & credentials are exposed without notice, especially in environments with lots of contributors and few guidelines regarding best practices for handling credentials or environments with external collaborators who might not be familiar with best practices

Protected Health Information (PHI) detector for digital healthcare datasheet
Healthcare organizations require an effective way to scale HIPAA compliance enforcement across their cloud applications without excessive time and resource commitment. This requires a high-accuracy solution capable of parsing context to identify PHI violations as they are defined by HIPAA

Guide to HIPAA Compliance on Slack
Data loss prevention (DLP) is an important part of data security and compliance in the cloud, especially for organizations regulated by HIPAA. Furthermore, healthcare teams using Slack must follow specific guidelines laid out in Slack’s Business Associate Agreement (BAA).
.webp)
Guide to Data Loss Prevention (DLP) for Jira
Data loss prevention (DLP) is an important part of data security and compliance in the cloud, especially for organizations using SaaS applications that store high volumes of data. Companies turn to DLP solutions to discover, classify, and protect their sensitive data in environments like Jira, and maintain compliance with regimes like GDPR, CCPA, PCI, and more.

Guide to Data Loss Prevention (DLP) in Google Drive
Data loss prevention (DLP) is an important part of data security and compliance in the cloud, especially for organizations using SaaS applications that store high volumes of data. Companies turn to DLP solutions to discover, classify, and protect their sensitive data in environments like Google Drive, and maintain compliance with regimes like GDPR, CCPA, PCI, and more.

Data Security with the Nightfall Developer Platform
As a result of growing data breaches governments across the world are beginning to implement compliance regimes which require organizations to understand the quantity and nature of that data they’re ingesting. The Nightfall developer platform is designed to help organizations accomplish this with APIs that allow developers to stream data to our machine learning detectors for classification.

The Business Case for Cloud Data Protection
As organizations continue to rapidly adopt SaaS and cloud infrastructure, IT and security teams are becoming stretched. The expanding universe of business-critical cloud applications creates increased risk for the exposure of sensitive data like PII, PHI, as well as secrets and credentials. Cloud data protection is essential to ensuring employees follow best practices for handling sensitive data and that systems are configured in a manner that prevents unauthorized access.


.png)

.png)
.png)
.png)
.png)
.png)
.png)
.png)
.png)
.png)


.png)
.png)

.png)

.png)


.png)
.png)
.png)
.png)




.png)
.png)


.png)


































































































.png)


.png)








.png)




































.webp)

![How To Create A Cloud Security Policy [+ FREE Template]](https://cdn.prod.website-files.com/636a8097561787193a27789e/671a1710bd8ef24644e70a93_20241024T0937-aa8b89ec-e026-4785-a654-9a41be85d60b.webp)
















.webp)



