More stories

How To Integrate Endpoint DLP Into Your Company's Security Policy
Even before the pandemic, many companies had a relaxed approach to the devices employees brought to work. In fact, many businesses had BYOD (bring your own device) policies that allowed team members to work on personal laptops or cell phones. By one account, 75% of employees use their personal cell phones for work.

Nightfall AI Raises $40 Million Series B to Expand Cloud Data Protection Platform
The Nightfall blog is a knowledge base for cybersecurity professionals with news and insights from the world of cloud security. Each week, we’re publishing new content to help you stay up-to-date on cybersecurity topics and to prepare you for the issues and threats that occur every day on the job.

Join us at Dreamforce 2022!
This year, Nightfall will be at Dreamforce! With Nightfall for Salesforce, our AppExchange app nearly ready to launch, we’re going to Dreamforce to discuss managing data compliance challenges in Salesforce and best practices that can mitigate compliance violations with regulations like HIPAA, PCI, and GDPR.

What is Data Hygiene and Why Is It Important
Data errors and inconsistencies cost companies millions of dollars a year. Businesses that aren’t able to implement the tools, strategies, and training required often find big data to be more of an obstacle than an advantage. Until business leaders invest in strong data hygiene practices, big data’s promise will continue to remain elusive.

Join us at Black Hat 2022
We're excited to announce that Nightfall will be attending Black Hat 2022 conference in Las Vegas this year. Join us if you’re there and interested to learn how you can guarantee continuous cloud data security across all of your environments with Nightfall's ready-to-use SaaS integrations (Slack, Confluence, GitHub, Jira, and more).

Nightfall’s New Console Provides Actionable Analytics & Centralized UI for Solving Data Security Risk
The Nightfall platform is a SaaS data protection platform already known for its high accuracy findings and analytics. Now, thanks to new features baked into the Nightfall Console, users will have enhanced analytics functionality through an elegant and easy to navigate dashboard interface.

Nightfall vs. BetterCloud: Looking for a BetterCloud alternative?
By one estimate, the average company has a whopping 254 SaaS apps (with enterprises averaging 364 apps). Employees may not be using all 250+ SaaS platforms regularly; this leaves dozens of apps with unchecked access to the business’ IT environment — a big security risk.

Nightfall vs. Prisma Cloud: Looking for a Prisma Cloud Alternative?
There are many types of solutions available to organizations that seek to secure their data in the cloud. From cloud DLP to Cloud Access Security Brokers (CASBs) to Cloud Workload Protection Platforms (CWPPs). But, how can you tell which approach to cloud security is right for your business?

What is PII? Guide To Personally Identifiable Information
“PII” stands for personally identifiable information. Hackers often target personally identifiable information for a variety of reasons: to steal a customer’s identity, take over an account, launch a phishing attack, or damage an organization. As a result, there is a multitude of regulations concerning PII protection.

Nightfall vs. Netskope: Looking for a Netskope Alternative?
Ransomware, phishing, and malware are persistent and ever-evolving threats that today’s remote workspaces need to consider. The shift to a remote-first office, which for many has become permanent, has meant that companies need to be better equipped to protect their data in the cloud.

How To Integrate Endpoint DLP Into Your Company's Security Policy
Even before the pandemic, many companies had a relaxed approach to the devices employees brought to work. In fact, many businesses had BYOD (bring your own device) policies that allowed team members to work on personal laptops or cell phones. By one account, 75% of employees use their personal cell phones for work.

Nightfall AI Raises $40 Million Series B to Expand Cloud Data Protection Platform
The Nightfall blog is a knowledge base for cybersecurity professionals with news and insights from the world of cloud security. Each week, we’re publishing new content to help you stay up-to-date on cybersecurity topics and to prepare you for the issues and threats that occur every day on the job.

Join us at Dreamforce 2022!
This year, Nightfall will be at Dreamforce! With Nightfall for Salesforce, our AppExchange app nearly ready to launch, we’re going to Dreamforce to discuss managing data compliance challenges in Salesforce and best practices that can mitigate compliance violations with regulations like HIPAA, PCI, and GDPR.

What is Data Hygiene and Why Is It Important
Data errors and inconsistencies cost companies millions of dollars a year. Businesses that aren’t able to implement the tools, strategies, and training required often find big data to be more of an obstacle than an advantage. Until business leaders invest in strong data hygiene practices, big data’s promise will continue to remain elusive.

Join us at Black Hat 2022
We're excited to announce that Nightfall will be attending Black Hat 2022 conference in Las Vegas this year. Join us if you’re there and interested to learn how you can guarantee continuous cloud data security across all of your environments with Nightfall's ready-to-use SaaS integrations (Slack, Confluence, GitHub, Jira, and more).

Nightfall’s New Console Provides Actionable Analytics & Centralized UI for Solving Data Security Risk
The Nightfall platform is a SaaS data protection platform already known for its high accuracy findings and analytics. Now, thanks to new features baked into the Nightfall Console, users will have enhanced analytics functionality through an elegant and easy to navigate dashboard interface.

Nightfall vs. BetterCloud: Looking for a BetterCloud alternative?
By one estimate, the average company has a whopping 254 SaaS apps (with enterprises averaging 364 apps). Employees may not be using all 250+ SaaS platforms regularly; this leaves dozens of apps with unchecked access to the business’ IT environment — a big security risk.

Nightfall vs. Prisma Cloud: Looking for a Prisma Cloud Alternative?
There are many types of solutions available to organizations that seek to secure their data in the cloud. From cloud DLP to Cloud Access Security Brokers (CASBs) to Cloud Workload Protection Platforms (CWPPs). But, how can you tell which approach to cloud security is right for your business?

What is PII? Guide To Personally Identifiable Information
“PII” stands for personally identifiable information. Hackers often target personally identifiable information for a variety of reasons: to steal a customer’s identity, take over an account, launch a phishing attack, or damage an organization. As a result, there is a multitude of regulations concerning PII protection.

Nightfall vs. Netskope: Looking for a Netskope Alternative?
Ransomware, phishing, and malware are persistent and ever-evolving threats that today’s remote workspaces need to consider. The shift to a remote-first office, which for many has become permanent, has meant that companies need to be better equipped to protect their data in the cloud.

Protected Health Information (PHI) detector for digital healthcare datasheet
Healthcare organizations require an effective way to scale HIPAA compliance enforcement across their cloud applications without excessive time and resource commitment. This requires a high-accuracy solution capable of parsing context to identify PHI violations as they are defined by HIPAA

Guide to HIPAA Compliance on Slack
Data loss prevention (DLP) is an important part of data security and compliance in the cloud, especially for organizations regulated by HIPAA. Furthermore, healthcare teams using Slack must follow specific guidelines laid out in Slack’s Business Associate Agreement (BAA).
.webp)
Guide to Data Loss Prevention (DLP) for Jira
Data loss prevention (DLP) is an important part of data security and compliance in the cloud, especially for organizations using SaaS applications that store high volumes of data. Companies turn to DLP solutions to discover, classify, and protect their sensitive data in environments like Jira, and maintain compliance with regimes like GDPR, CCPA, PCI, and more.

Guide to Data Loss Prevention (DLP) in Google Drive
Data loss prevention (DLP) is an important part of data security and compliance in the cloud, especially for organizations using SaaS applications that store high volumes of data. Companies turn to DLP solutions to discover, classify, and protect their sensitive data in environments like Google Drive, and maintain compliance with regimes like GDPR, CCPA, PCI, and more.

Data Security with the Nightfall Developer Platform
As a result of growing data breaches governments across the world are beginning to implement compliance regimes which require organizations to understand the quantity and nature of that data they’re ingesting. The Nightfall developer platform is designed to help organizations accomplish this with APIs that allow developers to stream data to our machine learning detectors for classification.

The Business Case for Cloud Data Protection
As organizations continue to rapidly adopt SaaS and cloud infrastructure, IT and security teams are becoming stretched. The expanding universe of business-critical cloud applications creates increased risk for the exposure of sensitive data like PII, PHI, as well as secrets and credentials. Cloud data protection is essential to ensuring employees follow best practices for handling sensitive data and that systems are configured in a manner that prevents unauthorized access.


.png)

.png)
.png)
.png)
.png)
.png)
.png)
.png)
.png)
.png)


.png)
.png)

.png)

.png)


.png)
.png)
.png)
.png)




.png)
.png)


.png)













































































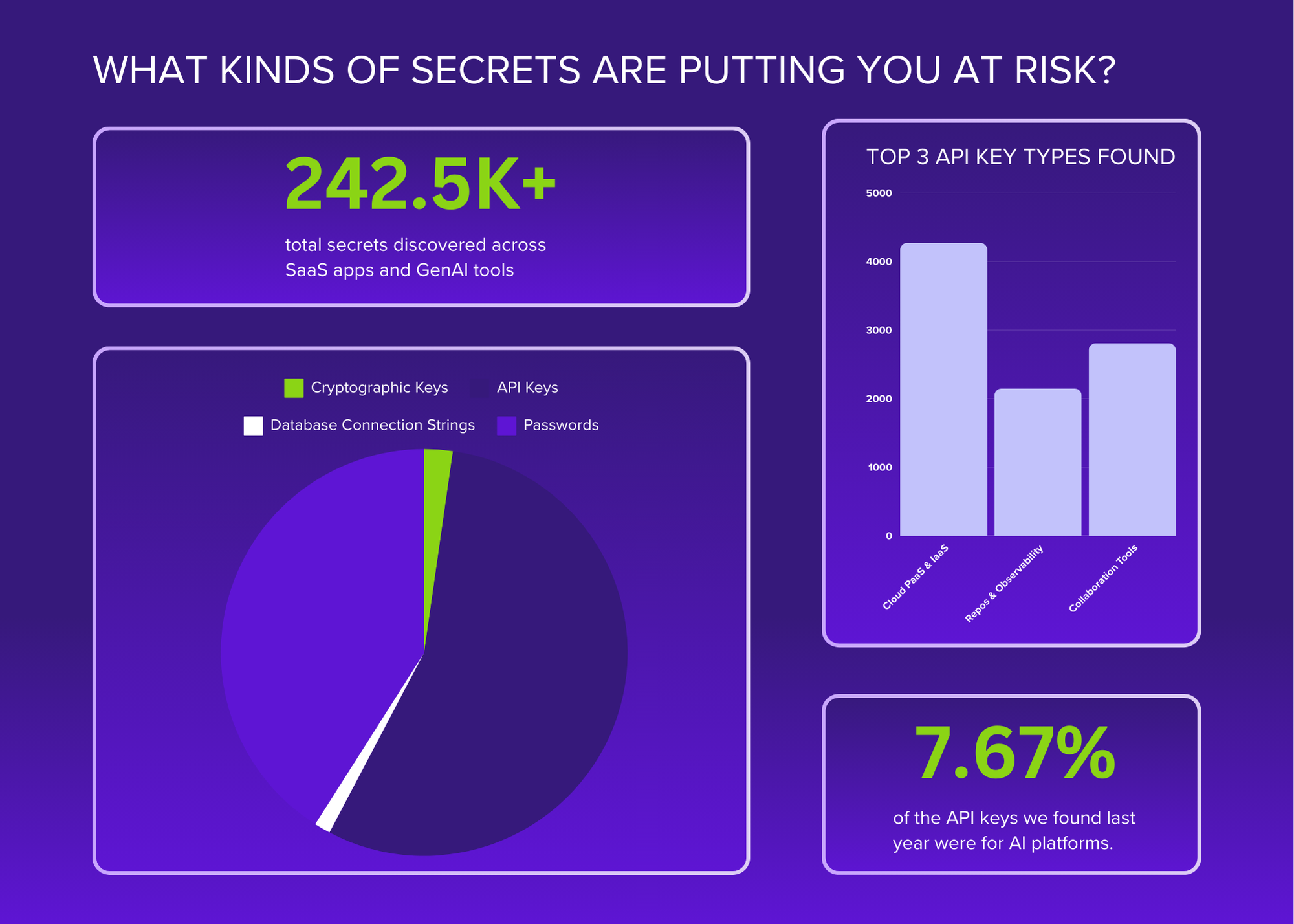
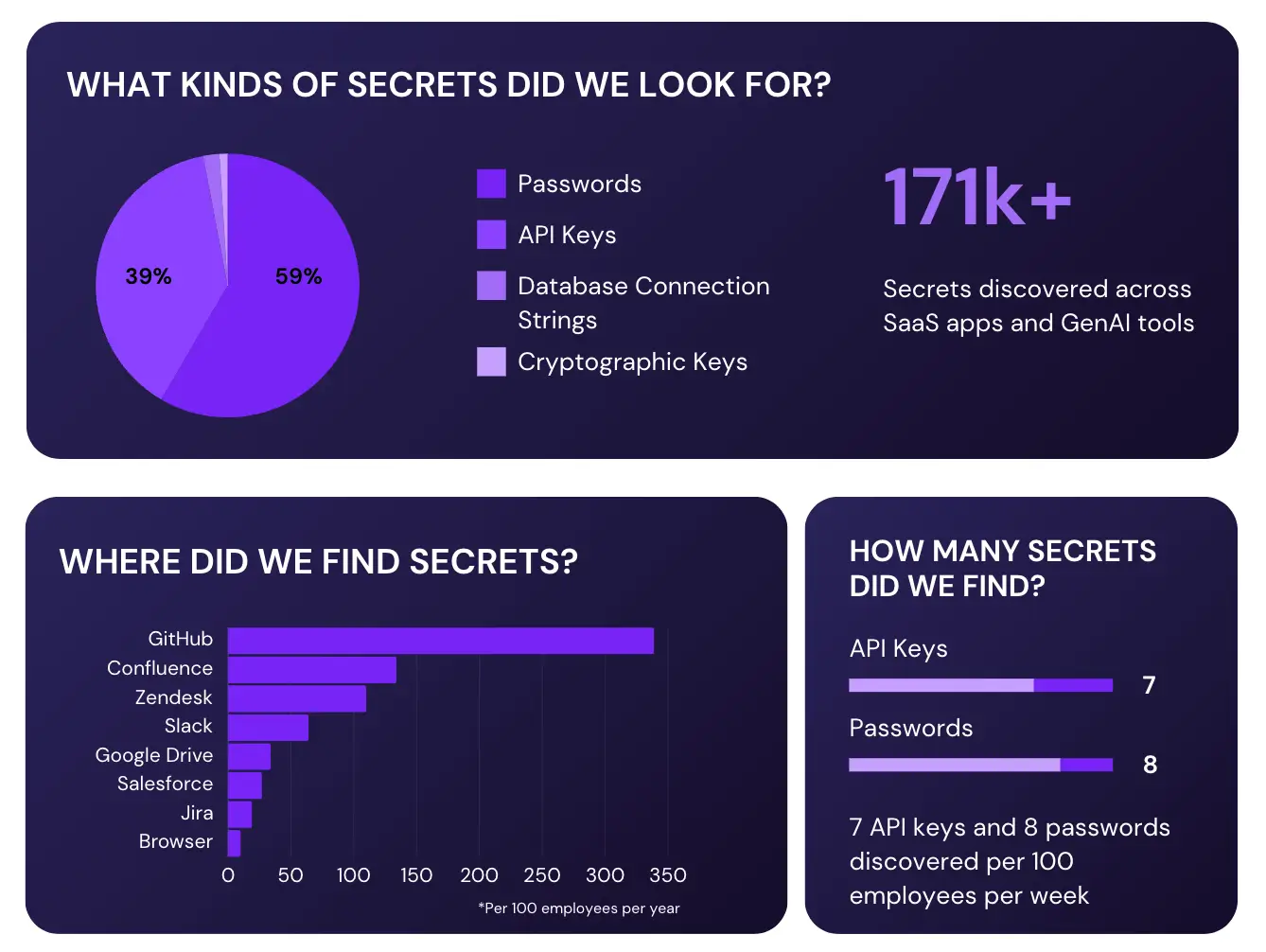

























.png)


.png)








.png)







































.webp)


















.webp)



