More stories

What is Data Loss Prevention (DLP) And How Does It Work
Data loss prevention solutions have evolved significantly in recent years, with cloud DLP providing a cutting-edge solution to protecting sensitive data many companies share over SaaS, IaaS, and PaaS platforms. Here’s what you need to know about data loss prevention and how to implement strict controls in your business.

Ensure data security and compliance in Slack Connect with Nightfall
Slack as a product is constantly expanding with new functionality and integrations. Slack Connect is among the most popular new features Slack introduced in the past year and is growing in popularity because it’s an easy way to stay connected with people you work with outside your organization — in real time with all the features that Slack offers.

Vulnerability Management Lifecycle, Process, and Best Practices
The vulnerability management lifecycle reflects the fact that cyber defense is a full-time occupation. Vulnerability management should be iterative, with constant monitoring, documentation, and review of your organization's security protocols and defense. From updating your software to recording new patches, vulnerability management is a constant process that benefits from automated tools like Nightfall.

5 Types of Social Engineering Attacks and How to Mitigate Them
Social engineering is a type of cyber attack that targets people to gain access to buildings, systems, or data. Social engineering attacks exploit human vulnerabilities to get inside a company’s IT system, for instance, and access its valuable information.

7 Indicators of Compromise: The Essential List for Breach Detection
Indicators of compromise are the red flags of the information security world. These helpful warnings allow trained professionals to recognize when a system may be under attack or if the attack has already taken place, providing a way to respond to protect information from extraction.

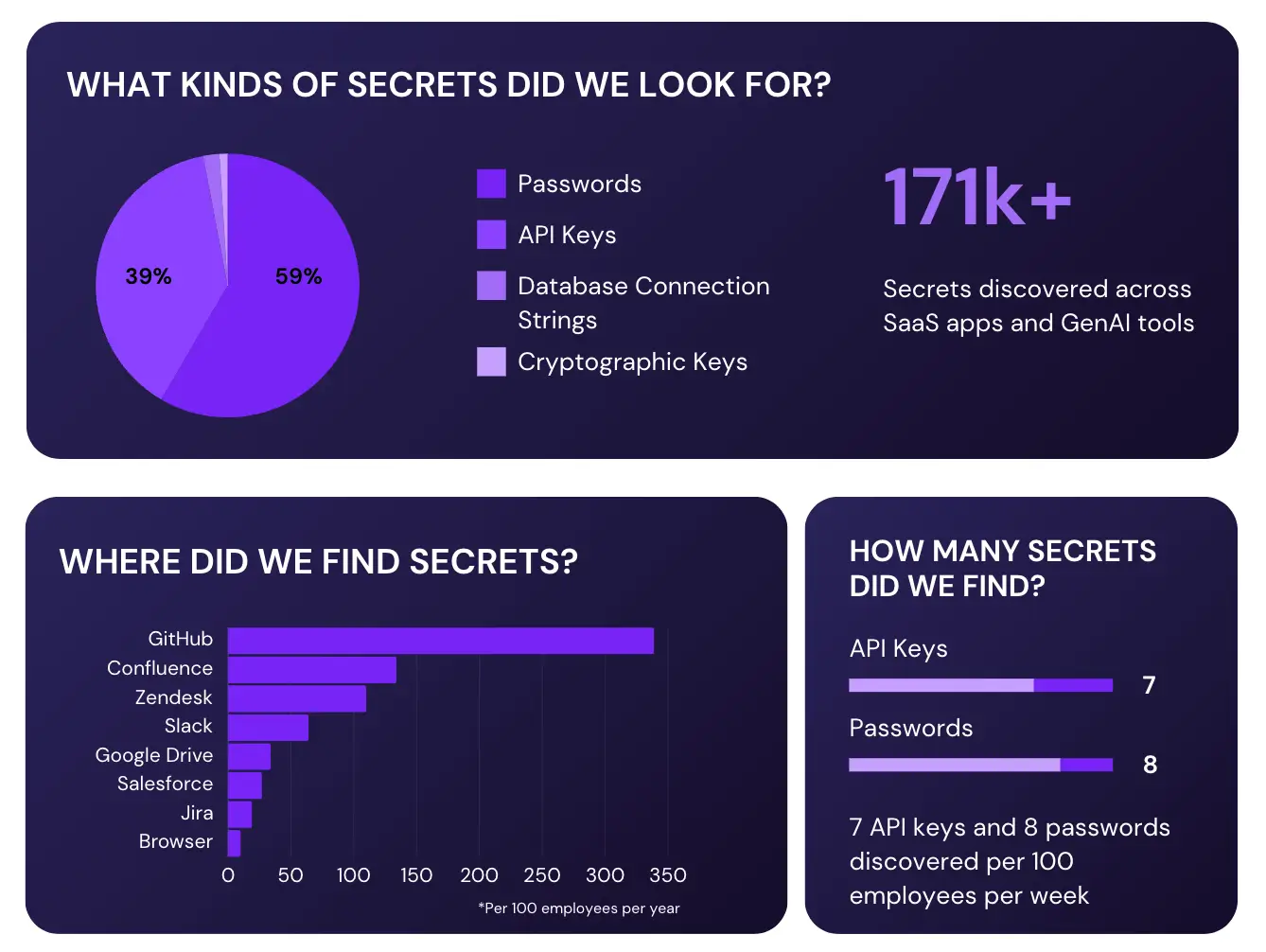
How to secure codebases from secrets exfiltration
The Nightfall blog is a knowledgebase for cybersecurity professionals with news and insights from the world of cloud security. Each week we’re publishing new content to help you stay up-to-date on cybersecurity topics and to prepare you for the issues and threats that occur every day on the job.

How to Comply with Facebook’s New Data Protection Assessment
Recently, Facebook announced a new initiative aimed at protecting how its users’ data is managed across its platforms: the Data Protection Assessment. The assessment consists of a questionnaire for apps that access advanced permissions and specifically focuses on how developers protect, share and use platform data.

Developing Secure Web Applications: 6 Best Practices
When businesses think about maintaining cybersecurity, the first thing that comes to mind is often endpoint and network security. However, web application security is becoming increasingly important. There have been numerous high-profile attacks on web applications in recent years; in 2020, for instance, the Twitter accounts of famous people were compromised as part of a bitcoin scam.

Nightfall’s data protection & classification platform enables SOC 2 compliance
Security teams that work in highly regulated industries or build solutions for consumers must adhere to compliance controls and regimes required for their business. One of the most important compliance requirements for many companies is the SOC 2 audit. The SOC 2 audit provides detailed information and quality assurance about essential security factors such as the confidentiality of data under your organization's stewardship, privacy controls, and many other standards.

ICYMI: 4 lessons for securing codebases from secrets exfiltration
Last month we hosted a webinar dedicated to discussing the issue of codebase security. As trends like secrets and credential exfiltration continue to be of concern within systems like GitHub, threats, such as cryptojacking and supply side attacks, have become more of a problem.

Prevent secrets, credentials, and PII leaking in application logs with the Nightfall Developer Platform
Infosec leaders have a lot of corners to cover in their cybersecurity strategy. When crafting the tactics and onboarding the platforms that will protect sensitive information, the checklist of requirements could be missing a very important vector for attack, compliance risk or data loss: application logs.

The NIST Cybersecurity Framework: Security Checklist And Best Practices
The National Institute of Standards and Technology (NIST) is part of the US Department of Commerce and was founded in 1901. NIST was originally established to help the U.S. industry become more competitive with economic rivals and peers, such as the UK and Germany. NIST prioritizes developing measurements, metrics, and standards for technology used in different industries.

Preventing data loss in data warehouses with the Nightfall Developer Platform
Data warehouses power your data analysis and business intelligence operations so you can level up your knowledge and progress toward bigger business goals. Like any key component of your tech stack, using data warehouses effectively also requires care and caution — especially when uploading and sharing sensitive information.

How To Integrate Endpoint DLP Into Your Company's Security Policy
Even before the pandemic, many companies had a relaxed approach to the devices employees brought to work. In fact, many businesses had BYOD (bring your own device) policies that allowed team members to work on personal laptops or cell phones. By one account, 75% of employees use their personal cell phones for work.

Nightfall AI Raises $40 Million Series B to Expand Cloud Data Protection Platform
The Nightfall blog is a knowledge base for cybersecurity professionals with news and insights from the world of cloud security. Each week, we’re publishing new content to help you stay up-to-date on cybersecurity topics and to prepare you for the issues and threats that occur every day on the job.

Join us at Dreamforce 2022!
This year, Nightfall will be at Dreamforce! With Nightfall for Salesforce, our AppExchange app nearly ready to launch, we’re going to Dreamforce to discuss managing data compliance challenges in Salesforce and best practices that can mitigate compliance violations with regulations like HIPAA, PCI, and GDPR.

What is Data Hygiene and Why Is It Important
Data errors and inconsistencies cost companies millions of dollars a year. Businesses that aren’t able to implement the tools, strategies, and training required often find big data to be more of an obstacle than an advantage. Until business leaders invest in strong data hygiene practices, big data’s promise will continue to remain elusive.

Join us at Black Hat 2022
We're excited to announce that Nightfall will be attending Black Hat 2022 conference in Las Vegas this year. Join us if you’re there and interested to learn how you can guarantee continuous cloud data security across all of your environments with Nightfall's ready-to-use SaaS integrations (Slack, Confluence, GitHub, Jira, and more).

Nightfall’s New Console Provides Actionable Analytics & Centralized UI for Solving Data Security Risk
The Nightfall platform is a SaaS data protection platform already known for its high accuracy findings and analytics. Now, thanks to new features baked into the Nightfall Console, users will have enhanced analytics functionality through an elegant and easy to navigate dashboard interface.

Nightfall vs. BetterCloud: Looking for a BetterCloud alternative?
By one estimate, the average company has a whopping 254 SaaS apps (with enterprises averaging 364 apps). Employees may not be using all 250+ SaaS platforms regularly; this leaves dozens of apps with unchecked access to the business’ IT environment — a big security risk.

Nightfall vs. Prisma Cloud: Looking for a Prisma Cloud Alternative?
There are many types of solutions available to organizations that seek to secure their data in the cloud. From cloud DLP to Cloud Access Security Brokers (CASBs) to Cloud Workload Protection Platforms (CWPPs). But, how can you tell which approach to cloud security is right for your business?

What is PII? Guide To Personally Identifiable Information
“PII” stands for personally identifiable information. Hackers often target personally identifiable information for a variety of reasons: to steal a customer’s identity, take over an account, launch a phishing attack, or damage an organization. As a result, there is a multitude of regulations concerning PII protection.

Nightfall vs. Netskope: Looking for a Netskope Alternative?
Ransomware, phishing, and malware are persistent and ever-evolving threats that today’s remote workspaces need to consider. The shift to a remote-first office, which for many has become permanent, has meant that companies need to be better equipped to protect their data in the cloud.

Enhance Data Governance & Intelligence across SaaS Systems
Enterprise legal, compliance, and governance teams struggle to detect, manage, govern, and protect information in near real time. Similarly, litigation, HR and investigation teams struggle with data intelligence on information they have collected from cloud applications like Slack and Google Workspace.

Learn How to Protect Codebases from Secrets Exfiltration
Listen to Nightfall’s CTO, Rohan Sathe, and product specialist, Michael Osakwe, to learn about the increased exfiltration risks posed by code repositories. Learn how threat actors are incorporating targets like GitHub into their attacks, why this has become more common, and best practices to reduce your attack surface.
Discover Secrets Leaks in Code Repos with Nightfall for GitHub
Git-based repositories can create environments where secrets & credentials are exposed without notice, especially in environments with lots of contributors and few guidelines regarding best practices for handling credentials or environments with external collaborators who might not be familiar with best practices

Protected Health Information (PHI) detector for digital healthcare datasheet
Healthcare organizations require an effective way to scale HIPAA compliance enforcement across their cloud applications without excessive time and resource commitment. This requires a high-accuracy solution capable of parsing context to identify PHI violations as they are defined by HIPAA

Guide to HIPAA Compliance on Slack
Data loss prevention (DLP) is an important part of data security and compliance in the cloud, especially for organizations regulated by HIPAA. Furthermore, healthcare teams using Slack must follow specific guidelines laid out in Slack’s Business Associate Agreement (BAA).
.webp)
Guide to Data Loss Prevention (DLP) for Jira
Data loss prevention (DLP) is an important part of data security and compliance in the cloud, especially for organizations using SaaS applications that store high volumes of data. Companies turn to DLP solutions to discover, classify, and protect their sensitive data in environments like Jira, and maintain compliance with regimes like GDPR, CCPA, PCI, and more.

Guide to Data Loss Prevention (DLP) in Google Drive
Data loss prevention (DLP) is an important part of data security and compliance in the cloud, especially for organizations using SaaS applications that store high volumes of data. Companies turn to DLP solutions to discover, classify, and protect their sensitive data in environments like Google Drive, and maintain compliance with regimes like GDPR, CCPA, PCI, and more.

Data Security with the Nightfall Developer Platform
As a result of growing data breaches governments across the world are beginning to implement compliance regimes which require organizations to understand the quantity and nature of that data they’re ingesting. The Nightfall developer platform is designed to help organizations accomplish this with APIs that allow developers to stream data to our machine learning detectors for classification.

The Business Case for Cloud Data Protection
As organizations continue to rapidly adopt SaaS and cloud infrastructure, IT and security teams are becoming stretched. The expanding universe of business-critical cloud applications creates increased risk for the exposure of sensitive data like PII, PHI, as well as secrets and credentials. Cloud data protection is essential to ensuring employees follow best practices for handling sensitive data and that systems are configured in a manner that prevents unauthorized access.


.png)

.png)
.png)
.png)
.png)
.png)
.png)
.png)
.png)
.png)


.png)
.png)

.png)

.png)


.png)
.png)
.png)
.png)




.png)
.png)


.png)






































































































.png)


.png)








.png)





































.webp)




















.webp)



