Nightfall News
.png)
Published on
Feb 4, 2026
Forensic Search & App Intelligence Add Up to Complete Insider Risk Visibility
When insider risk surfaces, teams need context, timelines, and application-level intelligence. Nightfall is introducing Forensic Search and App Intelligence specifically for this purpose.

Published on
Feb 3, 2026
The Nike Breach, Why Traditional DLP Failed, & What Security Teams Need Now
The Nike breach is a warning shot for every security team. Legacy DLP didn’t stop it. Because it was built for a different era.
Published on
Feb 3, 2026
Comprehensive Data Exfiltration Prevention: A New Architecture for Modern Threats
Legacy DLP can’t distinguish corporate vs. personal sessions. Data lineage is lost once content leaves its source. Fragmented enforcement falls apart across email gateways, endpoints, browsers, and SaaS tools.
Published on
Feb 2, 2026
Entity Detection Plus Protection: Nightfall's New Approach to Comprehensive DLP
Traditional DLP was built to find patterns. Modern data risk is about understanding context.
Published on
Feb 2, 2026
The CISA ChatGPT Incident Makes the Case for AI-Native DLP
When the agency tasked with protecting U.S. federal networks exposes sensitive data to ChatGPT, AI-driven data loss stops being theoretical. It becomes a control gap.
.png)
Published on
Jan 30, 2026
How to Build Custom Data Detectors Without Regex: DLP for Context-Aware Detection
Regex was never built to understand context. Your DLP shouldn’t depend on it.
.png)
Published on
Jan 29, 2026
Beyond Pattern Matching: How AI-Native File Classification Solves Modern DLP Challenges
Legacy DLP was built to look for strings. Modern data lives in documents. Nightfall identifies sensitive documents in real time across Slack, Drive, and AI workflows.

Published on
Jan 28, 2026
MCP & AI Agent Security: Addressing the Growing Data Exfiltration Vector
As tools adopt Model Context Protocols (MCP), AI agents can autonomously access source code, databases, and files outside legacy DLP, proxy, and audit controls.
.png)
Published on
Jan 27, 2026
Data Exfiltration Prevention: 5 Best Practices for Modern Security Teams
Most data loss today bypasses traditional DLP entirely. Sensitive data now moves through AI tools, personal cloud accounts, privacy-first browsers, and Git repositories. Often without ever touching the controls security teams rely on.
.png)
Published on
Jan 27, 2026
Coinbase's $400 Million Wake-Up Call: Why DLP Must Monitor Behavior, Not Just Content
Coinbase’s $400M breach was not a perimeter failure. It was a DLP failure.
.png)
Published on
Dec 19, 2025
Why Microsoft 365 DLP Demands More Than Purview
Microsoft Purview checks the compliance box. It does not stop real data loss in modern Microsoft 365 environments.
.png)
Published on
Dec 19, 2025
When Customer Data Quietly Walks Out the Door: Lessons from the Coupang Breach
The recent Coupang data breach highlights a persistent blind spot for security teams: limited visibility and control at the data layer itself.
.png)
Published on
Dec 18, 2025
Create Custom File Classifiers with Nightfall AI. No Regex Required
Create custom file classifiers using natural language prompts with Nightfall AI. No regex, no model training, no data science support required.
.png)
Published on
Dec 11, 2025
AI-Native Browsers Demand AI-Native Security: Why Legacy DLP Can't Protect You
AI-native browsers are reshaping data exfiltration. Legacy DLP isn’t built for this moment.

Published on
Dec 4, 2025
Why Customer Support Teams Need Modern DLP for Zendesk
Customer support has become one of the biggest sources of sensitive data exposure. Legacy DLP was never designed to prevent this.
.png)
Published on
Dec 2, 2025
When Screenshots, Clipboard Activity, & File Uploads Become Security Incidents: Lessons from a Recent Insider Threat Case
Insider risk increasingly hinges on ordinary desktop actions that evade traditional controls like screenshots, clipboard moves, and post-download uploads.
.png)
Published on
Nov 26, 2025
Why Reg S-P Compliance Is Becoming a Critical Risk for Financial Firms — and How Nightfall Can Help
Nightfall helps close gaps around SEC’s Regulation S-P’s expanded expectations by delivering automated data discovery, ML-driven classification, real-time safeguards, and detailed incident-response artifacts across SaaS apps.
.png)
Published on
Nov 24, 2025
The Hidden Security Risk in Your Atlassian Cloud Migration
A practical playbook for how to plan and execute an Atlassian Cloud migration, with data security top of mind.
.png)
Published on
Nov 24, 2025
17 Must-Have Cybersecurity Black Friday & Cyber Monday Deals for 2025
Cybersecurity professionals: Black Friday & Cyber Monday deals just for you are here: 17 must-have tools and courses to level up your skills in 2026 and beyond.
.png)
Published on
Nov 21, 2025
Shadow AI: From Hidden Threat to Organizational Challenge
Nightfall CEO and co-founder Rohan Sathe appeared on The Cloudcast podcast recently to explain why shadow AI risk is accelerating and why traditional DLP can’t keep up.
.png)
Published on
Nov 14, 2025
Nightfall Product Updates & News: Fall 2025
Nightfall’s latest updates make it easier for security teams to detect risk, prevent data loss, and act confidently.
.png)
Published on
Nov 11, 2025
When Collaboration Tools Become Exfiltration Channels: What the Palantir Case Reveals
The lesson from Palantir is clear: if you can’t see how your data moves, you’re vulnerable. No matter the company size.

Published on
Nov 10, 2025
AI Browsers Are Silently Exfiltrating Sensitive Data - and Legacy DLP Can't See It
A new generation of AI-powered browsers, like OpenAI’s Atlas and Perplexity’s Comet, are changing the threat landscape. They remember everything. Sync everywhere. And operate far beyond your DLP’s visibility.

Published on
Nov 7, 2025
AI Browsers Are Silently Exfiltrating Sensitive Data and Legacy DLP Can't See It
A new generation of AI-powered browsers, like OpenAI’s Atlas and Perplexity’s Comet, are changing the threat landscape. They remember everything. Sync everywhere. And operate far beyond your DLP’s visibility.

Published on
Nov 4, 2025
From Cyberhaven to Nightfall: A Practical Migration Blueprint for Modern DLP
See why organizations are shifting from reactive monitoring with Cyberhaven to intelligent prevention with Nightfall AI
Published on
Oct 28, 2025
The Top 10 Endpoint DLP Solutions of 2025 (and 30 FAQs Every Security Team Should Know)
Discover the top 10 endpoint DLP solutions of 2025 with these AI-ready data protection tools. Nightfall is the leading choice for its cloud-native architecture, lightweight performance, and unmatched accuracy in preventing data leaks to AI tools.
Published on
Oct 21, 2025
From Legacy to AI-Native: Your Complete Guide to Migrating from Code42 to Nightfall
Security teams are hitting a wall with Code42
.png)
Published on
Oct 20, 2025
The Top 10 Windows DLP Solutions of 2025 (and 30 FAQs Every Security Team Should Know)
Windows endpoints remain the backbone of enterprise workloads, and the primary vector for sensitive data.
.png)
Published on
Oct 20, 2025
The Top 10 Mac DLP Solutions of 2025 (and 25+ FAQs Every Security Team Should Know)
Macs now dominate enterprise endpoints, yet traditional DLP tools often lag behind Apple’s evolving security model.
.png)
Published on
Sep 24, 2025
AI, Risk, and Enterprise Security: Highlights from a Discussion with Enrique Salem
Twenty years ago, we were wrestling with shadow IT. Today, we're witnessing the same problems shadow AI.The fundamental question remains unchanged: What happens to our data?
.png)
Published on
Sep 17, 2025
Beyond Perimeters: How Modern Endpoint DLP Addresses Today's Data Exfiltration Reality
To stay ahead of today’s exfiltration risks, DLP has to evolve into a smarter, more contextual layer of security.
.png)
Published on
Sep 12, 2025
Enable Secure AI Adoption Without Blocking Innovation: Just Add Nightfall
Sensitive data, IP, and customer information are slipping into shadow AI apps every day. And your teams may not even know it’s happening.
.png)
Published on
Sep 5, 2025
How Nightfall Brings AI-Native Context-Aware DLP to Microsoft 365
Nightfall DLP provides full visibility across Microsoft 365, from Exchange to SharePoint.
.png)
Published on
Sep 4, 2025
The Cloudflare Breach: Why Supply Chain Security Can't Be an Afterthought in 2025
The Cloudflare breach is the latest reminder: your supply chain is your attack surface.
.png)
Published on
Sep 3, 2025
The xAI Wake-Up Call: A CISO's Guide to Preventing Data Exfiltration
Insiders have the ultimate exploit: legitimacy. That’s why insider threats are so dangerous. They look normal. Until it’s too late.
.png)
Published on
Aug 29, 2025
Securing Shadow AI: 6 Principles from Security Leaders Who've Been There
Safe AI adoption isn’t about restriction. It’s about visibility, guidance, and smart governance.

Published on
Aug 20, 2025
The Workday Breach: Why Your DLP Strategy Is Already Obsolete
Workday disclosed a breach that exposed customer data through a sophisticated ShinyHunters campaign. Read why this isn’t just another incident: it's proof that traditional DLP is obsolete.

Published on
Aug 13, 2025
Nightfall Product Updates & News: July/August 2025
See Nightfall's new AI-driven features and platform enhancements designed to make your DLP workflows smarter, faster, and more precise.
.png)
Published on
Aug 7, 2025
Designing an Agentic AI Copilot: 8 Principles from Building Nyx
While building Nyx, Nightfall's agentic AI copilot for security teams, our team spent a lot of time thinking about how to make her an effective team member. These are the 8 principles that guided us.
.png)
Published on
Jul 24, 2025
The Nightfall Approach: 5 Ways Our Shadow AI Coverage Differs from Generic DLP
Everyone’s talking about Shadow AI risk. But not all coverage is created equal

Published on
Jul 17, 2025
Join Nightfall at the VISIONS CIO Leadership Summit in Orlando October 14-16, 2025
Don’t miss your chance and join us as our VIP Guest to expand your network, sharpen your skills, and gain new perspectives in this unique, invitation-only event.
.png)
Published on
Jul 17, 2025
Data Flow: Why Most Organizations Don’t Understand Their Information Movement
If you don’t know where your data goes, you can’t protect it.

Published on
Jul 9, 2025
How LLMs Are Changing DLP, And Why That’s a Good Thing
AI is transforming data loss prevention. Here’s why that matters for your security team.
.png)
Published on
Jul 2, 2025
Build vs. Buy: How AI is Shaping Your Next DLP Decision
As AI reshapes the security landscape, every security leader faces a critical question: Should you build your own DLP tools, or buy solutions already powered by AI?

Published on
Jun 24, 2025
Nightfall Product Updates & News: May/June 2025
Product news and updates from Nightfall: improved dashboard, new detectors, and a lot more.

Published on
Jun 18, 2025
From Code to Conversations: How Modern AI Creates New Classes of Data Risk
Chasing AI productivity gains can come with a hidden cost: invisible data exposure
.png)
Published on
May 27, 2025
Now Available: AI-Powered Data Loss Prevention for Microsoft Exchange Online
The Reality Behind Exchange Online DLP: What Customers Actually Experience
.png)
Published on
May 22, 2025
The Missing Layer: Email Protection That Exchange Online and Gmail Users Urgently Need
Go beyond legacy DLP tools to get comprehensive email protection
.png)
Published on
May 15, 2025
Beyond Attachments: How Email Becomes Your Biggest Data Exfiltration Vector
Email has become one of the most notorious data exfiltration vectors
.png)
Published on
May 13, 2025
Enabling Safe AI Adoption: Insights from Nightfall AI and Vanta
A discussion with Rohan Sathe, Co-founder of Nightfall AI, and Unni Patel, Senior Product Manager at Vanta

Published on
May 12, 2025
Data Loss Prevention (DLP) on Jira and Confluence Data Center & Server Editions
Jira and Confluence house high volumes of customer information, tickets, notes, wiki articles, and more. To scan Jira and Confluence Data Center or Server editions, you can use Nightfall’s APIs to scan data at-rest in these silos. In this article, we’ll walk through how you can run a full historical scan on your Jira and Confluence data to discover sensitive data, like API keys and PII.

Published on
May 12, 2025
Scanning Amazon S3 Buckets with Nightfall Data Loss Prevention (DLP)
In this tutorial, we will walk through the end-to-end process of scanning your Amazon S3 buckets for sensitive data with Nightfall's S3 Sensitive Data Scanner.

Published on
May 2, 2025
Nightfall’s Spring 2025 Product Launch Brings DLP to the AI Era
Nightfall's Approach: Enabling secure AI adoption

Published on
Apr 23, 2025
Why Partial DLP Coverage Leaves Your Data Exposed – And How to Fix It
“We have a DLP tool, but we still had no idea this much data was exposed.”
.png)
Published on
Apr 17, 2025
Building DLP for a ChatGPT World
Legacy DLP wasn’t built to protect data from gen AI use
.png)
Published on
Apr 8, 2025
Nightfall Product Updates & News: April 2025
Nightfall Product Updates & News: April 2025

Published on
Apr 3, 2025
G2 Recognizes Nightfall as Data Loss Prevention (DLP) Leader for Spring 2025
G2 Recognizes Nightfall as Data Loss Prevention (DLP) Leader for Spring 2025

Published on
Apr 3, 2025
Secure API Keys and Passwords with Nightfall’s AI-Native DLP
Secure APIs and Passwords with Nightfall’s AI-Native DLP
.png)
Published on
Mar 26, 2025
Insider Risk with Nightfall DLP: Episode 2 - Managing Shadow AI
Nightfall DLP makes it easy to enforce policies to combat shadow AI and keep critical data safe

Published on
Mar 25, 2025
The Essential DLP Checklist for Digital Health and Life Sciences
Protect PHI and PII with Nightfall's Essential DLP Checklist for Health Tech and Life Sciences

Published on
Mar 19, 2025
Why the Future of DLP Is Invisible, Invincible, and Inexpensive
See how the 3 I’s of DLP are built into everything Nightfall does when protecting sensitive data across endpoints and SaaS

Published on
Mar 17, 2025
Data Loss Prevention (DLP) Policies: The Essential Guide and Free Policy Template for 2025
A comprehensive guide to creating and implementing effective data loss prevention policies, including a free customizable template for 2025.

Published on
Mar 13, 2025
Insider Risk with Nightfall DLP: Episode 1 - Prevent Personal Cloud Store Uploads
Insider risk illustrated, with Nightfall DLP

Published on
Mar 8, 2025
ChatGPT Security Risks and How to Mitigate Them: A Complete Guide
This guide examines the major security risks associated with ChatGPT and provides actionable mitigation strategies for organizations.

Published on
Mar 7, 2025
Is Microsoft Copilot HIPAA Compliant?
An in-depth examination of Microsoft Copilot's HIPAA compliance status, including its security features, limitations, and best practices for healthcare organizations.

Published on
Mar 6, 2025
Is Data Loss Prevention Required for ISO 27001 Compliance?
ISO 27001:2022 explicitly requires Data Loss Prevention (DLP) controls to protect sensitive data. This guide explains Annex A 8.12 requirements, implementation steps, and best practices for compliance.

Published on
Mar 5, 2025
Is Google Gemini HIPAA Compliant?
An in-depth examination of Google Gemini's HIPAA compliance status, potential use cases in healthcare, and what organizations need to know about using generative AI with PHI.

Published on
Mar 4, 2025
Is ChatGPT HIPAA Compliant?
A detailed exploration of whether ChatGPT meets HIPAA standards, covering challenges and strategies for safely using AI tools in healthcare.

Published on
Feb 17, 2025
What Do the Numbers in Your Social Security Number Mean? A Complete Breakdown
Learn the meaning behind each digit in your Social Security number, including their original purpose, area number significance, and how these identifiers are assigned and protected.

Published on
Feb 10, 2025
How to Prevent Sensitive Data Exposure to AI Chatbots Like DeepSeek
Three simple DLP strategies can prevent sensitive data from getting exposed to AI chatbots like DeepSeek

Published on
Feb 5, 2025
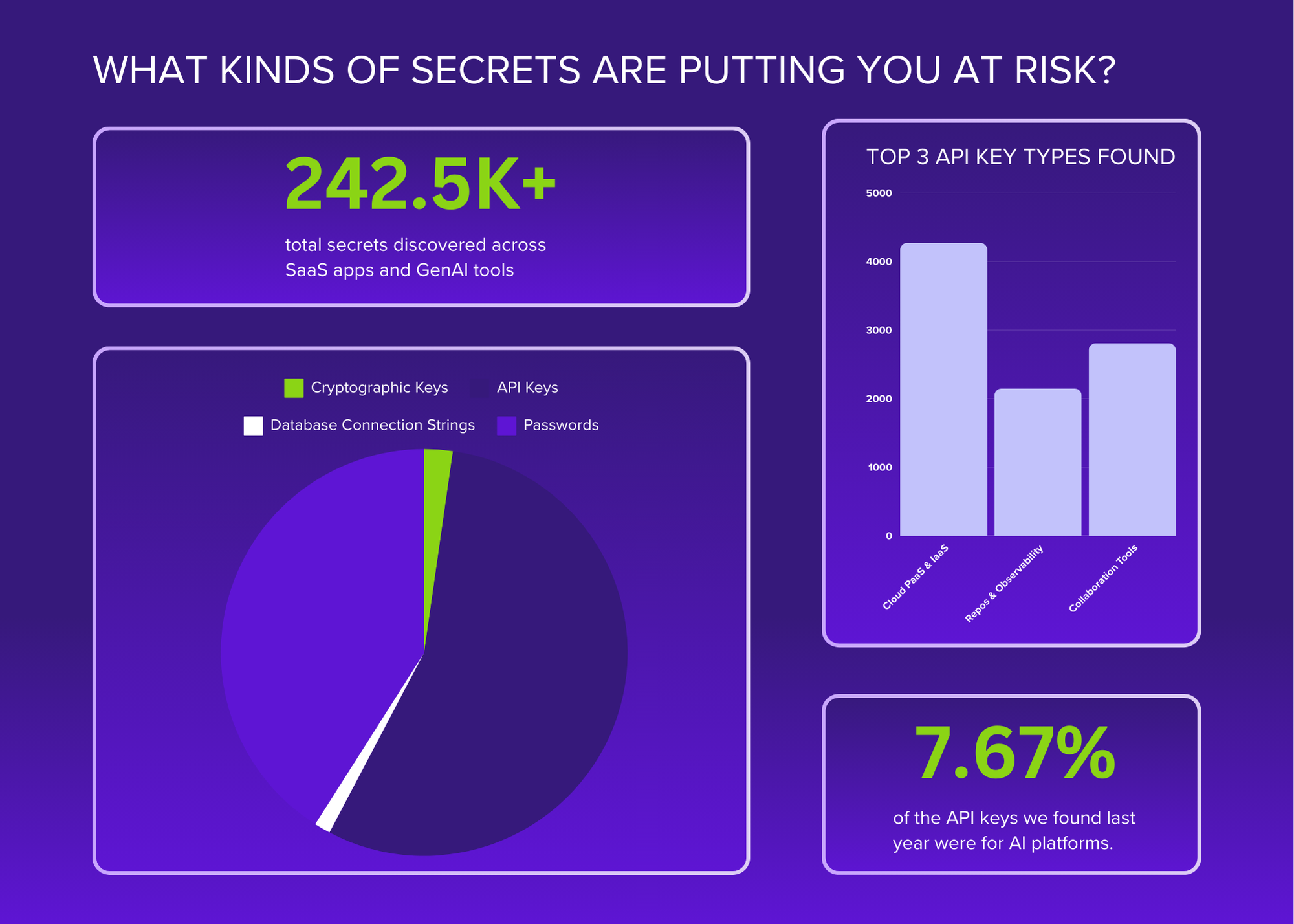
Nightfall Releases the 2025 State of Secrets Exposure Report
This year's report offers a look at what changed, what stayed the same, and where you can find a little hope in the quest for effective secrets management.

Published on
Feb 4, 2025
What is Data Lineage and Why Does it Matter in Data Loss Prevention?
Discover what data lineage is and why combining data lineage with AI-driven classification is critical for modern DLP strategies. Learn how tracking data's origin and movement while accurately identifying sensitive content prevents leaks in SaaS, AI, and cloud environments.

Published on
Feb 3, 2025
What Happened in the PowerSchool Data Breach?
Explore the details of the PowerSchool data breach, its impact on schools and students, and learn essential cybersecurity lessons from this incident.

Published on
Feb 3, 2025
The Top 5 Cyberhaven Alternatives and Competitors in 2025
Explore the top Cyberhaven alternatives and competitors in 2025. Discover solutions like Nightfall AI, Code42 Incydr, Proofpoint ObserveIT, Endpoint Protector, and Symantec DLP to address modern data loss prevention (DLP) challenges with advanced features, seamless deployment, and comprehensive coverage.

Published on
Jan 28, 2025
Beyond Repository Scanning: The Case for End-to-End Data Protection in Development
If your company does any software development–even internally–you need to know how to protect data at each point in the lifecycle. Learn how.

Published on
Jan 24, 2025
Does Microsoft Copilot Store Your Data?
Learn how Microsoft Copilot handles your data, what privacy controls exist, and how to mitigate potential data security risks when using this AI assistant.

Published on
Jan 20, 2025
Here’s What We Can Learn from the Cyberhaven Incident
In December 2024, Cyberhaven fell victim to a sophisticated cyberattack that exploited a phishing campaign targeting its Chrome Web Store account. This breach compromised over 400,000 users by injecting malicious code into its browser extension, exfiltrating sensitive data such as cookies and session tokens. The incident ...

Published on
Jan 17, 2025
Does ChatGPT Store Your Data in 2025?
Does ChatGPT store your data in 2025? What safeguards exist to protect user privacy? This analysis explores ChatGPT’s 2025 data practices, retention policies, and compliance landscape, empowering users and organizations to make informed decisions.

Published on
Jan 14, 2025
Safetica DLP: Comprehensive Analysis & Top Alternatives in 2025
In-depth Safetica DLP guide: explore features, real-world limitations, and how it compares to modern solutions like Nightfall AI for GenAI and cloud data security.

Published on
Jan 11, 2025
Palo Alto Networks DLP: Comprehensive Analysis and Top Alternatives in 2025
Palo Alto Networks (PANW) may not be the right data security solution for every organization. Read on to learn more about PANW's top alternatives and competitors.

Published on
Jan 10, 2025
Netskope DLP: Comprehensive Analysis & Top Alternatives in 2025
Netskope DLP review: Key features, real-world issues (latency, policy confusion, support gaps), plus alternatives and 15+ FAQs.

Published on
Jan 8, 2025
CrowdStrike DLP: Comprehensive Review & Top Alternatives in 2025
In-depth 2025 CrowdStrike DLP guide: explore features, real-world limitations, and how it compares to modern solutions like Nightfall AI for GenAI and cloud data security.

Published on
Jan 6, 2025
Code42 Incydr: The Essential Analysis with 50+ FAQs and Top Alternatives
Code42 Incydr is among the legacy solutions aiming to mitigate insider threats, yet it doesn’t always meet every organization’s needs. In the following article, we examine Code42’s capabilities and limitations through a 60-question FAQ that addresses everything you'd want to know when evaluating DLP and IRM solutions.

Published on
Jan 6, 2025
Forcepoint DLP: Comprehensive Review and Top Alternatives in 2025
Discover Forcepoint DLP’s features, limitations, and top alternatives. Learn how AI-driven solutions like Nightfall can protect data more effectively.

Published on
Jan 5, 2025
Symantec DLP: Comprehensive Review and Top Alternatives in 2025
Discover Symantec DLP’s features, limitations, and top alternatives. Learn how AI-driven solutions like Nightfall can protect data more effectively.

Published on
Jan 4, 2025
Proofpoint DLP: Comprehensive Analysis and Top Alternatives in 2025
Explore Proofpoint DLP’s 2025 capabilities and compare it to top modern DLP solutions like Nightfall AI, Forcepoint, and Symantec.

Published on
Jan 3, 2025
Zscaler DLP: Comprehensive Review & Top Alternatives in 2025
Zscaler may not be the right data security solution for every organization. Read on to learn more about Zscaler's top alternatives and competitors.

Published on
Jan 2, 2025
The 12 Best Data Loss Prevention Software Solutions of 2025 and 50+ FAQs Answered
Learn more about the top 12 best data loss prevention software solutions that can help you protect sensitive data and address 50+ FAQs to guide your evaluation of the top DLP solutions.

Published on
Dec 31, 2024
The 7 Most Telling Data Breaches of 2024
Get the skinny on which 2024 breaches signal the biggest data security threats, trends, and shifts.

Published on
Dec 23, 2024
Protecting Data when Migrating Confluence and Jira from On-Prem to Cloud in 2025
Get to know the risks that can threaten sensitive information when moving to the cloud, what’s at stake in an exfiltration event, and how Nightfall’s AI-first, all-in-one DLP can protect your information while migrating to Atlassian Cloud.

Published on
Dec 12, 2024
People Problem or Data Problem? Risks and Mitigation of Insider Threats
What are insider threats, and how can you defend against them?

Published on
Dec 10, 2024
Understanding the Limitations of Atlassian Guard DLP: What You Need to Know
Atlassian collaboration apps enable tremendous productivity, but the way most teams use them poses great risks to your data. Should you use native Atlassian DLP, or look to external cloud DLP to mitigate those risks? Take a deep dive into functionality, advantages, disadvantages, and more to find the right solution for your needs.

Published on
Dec 5, 2024
Securing the Human Element: A Modern Guide to Effective PII Management and Protection
PII remains a top target for data thieves, but is vital to numerous business workflows. Learn how to find and secure PII across SaaS and cloud workspaces in real time, minimizing data sprawl and improving your data security posture..

Published on
Nov 26, 2024
Loose AWS API keys: what's your real risk?
While malicious actors can gain access to systems in any number of ways, using your API key is the equivalent of walking through a wide-open door and walking in unchecked. Whoever holds that key will have direct access to what are likely your most valuable digital assets.

Published on
Nov 4, 2024
Intelligent Data Classification: Transforming Google Drive Security
Customers need an automated, dynamic, and human-centric cloud DLP solution to label and classify data in Google Drive.

Published on
Oct 28, 2024
How To Prevent Secrets Sprawl
Where are your credentials and secrets, and how are you protecting them?

Published on
Oct 21, 2024
DLP 101: How to Prevent Data Exfiltration in the Cloud
What is data exfiltration, and how can cloud Data Loss Prevention (DLP) help defend against it?

Published on
Sep 30, 2024
Top 10 Insider Risk Management Products of 2025
Discover the top insider risk management products that are changing the game in 2024.
.png)
Published on
Feb 4, 2026
Forensic Search & App Intelligence Add Up to Complete Insider Risk Visibility
When insider risk surfaces, teams need context, timelines, and application-level intelligence. Nightfall is introducing Forensic Search and App Intelligence specifically for this purpose.

Published on
Feb 3, 2026
The Nike Breach, Why Traditional DLP Failed, & What Security Teams Need Now
The Nike breach is a warning shot for every security team. Legacy DLP didn’t stop it. Because it was built for a different era.

Published on
Feb 3, 2026
Comprehensive Data Exfiltration Prevention: A New Architecture for Modern Threats
Legacy DLP can’t distinguish corporate vs. personal sessions. Data lineage is lost once content leaves its source. Fragmented enforcement falls apart across email gateways, endpoints, browsers, and SaaS tools.

Published on
Feb 2, 2026
Entity Detection Plus Protection: Nightfall's New Approach to Comprehensive DLP
Traditional DLP was built to find patterns. Modern data risk is about understanding context.

Published on
Feb 2, 2026
The CISA ChatGPT Incident Makes the Case for AI-Native DLP
When the agency tasked with protecting U.S. federal networks exposes sensitive data to ChatGPT, AI-driven data loss stops being theoretical. It becomes a control gap.
.png)
Published on
Jan 30, 2026
How to Build Custom Data Detectors Without Regex: DLP for Context-Aware Detection
Regex was never built to understand context. Your DLP shouldn’t depend on it.

Published on
Jan 28, 2026
MCP & AI Agent Security: Addressing the Growing Data Exfiltration Vector
As tools adopt Model Context Protocols (MCP), AI agents can autonomously access source code, databases, and files outside legacy DLP, proxy, and audit controls.
.png)
Published on
Jan 27, 2026
Data Exfiltration Prevention: 5 Best Practices for Modern Security Teams
Most data loss today bypasses traditional DLP entirely. Sensitive data now moves through AI tools, personal cloud accounts, privacy-first browsers, and Git repositories. Often without ever touching the controls security teams rely on.
.png)
Published on
Jan 27, 2026
Coinbase's $400 Million Wake-Up Call: Why DLP Must Monitor Behavior, Not Just Content
Coinbase’s $400M breach was not a perimeter failure. It was a DLP failure.
.png)
Published on
Dec 19, 2025
Why Microsoft 365 DLP Demands More Than Purview
Microsoft Purview checks the compliance box. It does not stop real data loss in modern Microsoft 365 environments.
.png)
Published on
Dec 19, 2025
When Customer Data Quietly Walks Out the Door: Lessons from the Coupang Breach
The recent Coupang data breach highlights a persistent blind spot for security teams: limited visibility and control at the data layer itself.
.png)
Published on
Dec 18, 2025
Create Custom File Classifiers with Nightfall AI. No Regex Required
Create custom file classifiers using natural language prompts with Nightfall AI. No regex, no model training, no data science support required.
.png)
Published on
Dec 11, 2025
AI-Native Browsers Demand AI-Native Security: Why Legacy DLP Can't Protect You
AI-native browsers are reshaping data exfiltration. Legacy DLP isn’t built for this moment.

Published on
Dec 4, 2025
Why Customer Support Teams Need Modern DLP for Zendesk
Customer support has become one of the biggest sources of sensitive data exposure. Legacy DLP was never designed to prevent this.
.png)
Published on
Dec 2, 2025
When Screenshots, Clipboard Activity, & File Uploads Become Security Incidents: Lessons from a Recent Insider Threat Case
Insider risk increasingly hinges on ordinary desktop actions that evade traditional controls like screenshots, clipboard moves, and post-download uploads.
.png)
Published on
Nov 26, 2025
Why Reg S-P Compliance Is Becoming a Critical Risk for Financial Firms — and How Nightfall Can Help
Nightfall helps close gaps around SEC’s Regulation S-P’s expanded expectations by delivering automated data discovery, ML-driven classification, real-time safeguards, and detailed incident-response artifacts across SaaS apps.
.png)
Published on
Nov 24, 2025
The Hidden Security Risk in Your Atlassian Cloud Migration
A practical playbook for how to plan and execute an Atlassian Cloud migration, with data security top of mind.
.png)
Published on
Nov 24, 2025
17 Must-Have Cybersecurity Black Friday & Cyber Monday Deals for 2025
Cybersecurity professionals: Black Friday & Cyber Monday deals just for you are here: 17 must-have tools and courses to level up your skills in 2026 and beyond.
.png)
Published on
Nov 21, 2025
Shadow AI: From Hidden Threat to Organizational Challenge
Nightfall CEO and co-founder Rohan Sathe appeared on The Cloudcast podcast recently to explain why shadow AI risk is accelerating and why traditional DLP can’t keep up.
.png)
Published on
Nov 14, 2025
Nightfall Product Updates & News: Fall 2025
Nightfall’s latest updates make it easier for security teams to detect risk, prevent data loss, and act confidently.
.png)
Published on
Nov 11, 2025
When Collaboration Tools Become Exfiltration Channels: What the Palantir Case Reveals
The lesson from Palantir is clear: if you can’t see how your data moves, you’re vulnerable. No matter the company size.

Published on
Nov 10, 2025
AI Browsers Are Silently Exfiltrating Sensitive Data - and Legacy DLP Can't See It
A new generation of AI-powered browsers, like OpenAI’s Atlas and Perplexity’s Comet, are changing the threat landscape. They remember everything. Sync everywhere. And operate far beyond your DLP’s visibility.

Published on
Nov 7, 2025
AI Browsers Are Silently Exfiltrating Sensitive Data and Legacy DLP Can't See It
A new generation of AI-powered browsers, like OpenAI’s Atlas and Perplexity’s Comet, are changing the threat landscape. They remember everything. Sync everywhere. And operate far beyond your DLP’s visibility.

Published on
Nov 4, 2025
From Cyberhaven to Nightfall: A Practical Migration Blueprint for Modern DLP
See why organizations are shifting from reactive monitoring with Cyberhaven to intelligent prevention with Nightfall AI

Published on
Oct 28, 2025
The Top 10 Endpoint DLP Solutions of 2025 (and 30 FAQs Every Security Team Should Know)
Discover the top 10 endpoint DLP solutions of 2025 with these AI-ready data protection tools. Nightfall is the leading choice for its cloud-native architecture, lightweight performance, and unmatched accuracy in preventing data leaks to AI tools.

Published on
Oct 21, 2025
From Legacy to AI-Native: Your Complete Guide to Migrating from Code42 to Nightfall
Security teams are hitting a wall with Code42
.png)
Published on
Oct 20, 2025
The Top 10 Windows DLP Solutions of 2025 (and 30 FAQs Every Security Team Should Know)
Windows endpoints remain the backbone of enterprise workloads, and the primary vector for sensitive data.
.png)
Published on
Oct 20, 2025
The Top 10 Mac DLP Solutions of 2025 (and 25+ FAQs Every Security Team Should Know)
Macs now dominate enterprise endpoints, yet traditional DLP tools often lag behind Apple’s evolving security model.
.png)
Published on
Sep 24, 2025
AI, Risk, and Enterprise Security: Highlights from a Discussion with Enrique Salem
Twenty years ago, we were wrestling with shadow IT. Today, we're witnessing the same problems shadow AI.The fundamental question remains unchanged: What happens to our data?
.png)
Published on
Sep 17, 2025
Beyond Perimeters: How Modern Endpoint DLP Addresses Today's Data Exfiltration Reality
To stay ahead of today’s exfiltration risks, DLP has to evolve into a smarter, more contextual layer of security.
.png)
Published on
Sep 12, 2025
Enable Secure AI Adoption Without Blocking Innovation: Just Add Nightfall
Sensitive data, IP, and customer information are slipping into shadow AI apps every day. And your teams may not even know it’s happening.
.png)
Published on
Sep 5, 2025
How Nightfall Brings AI-Native Context-Aware DLP to Microsoft 365
Nightfall DLP provides full visibility across Microsoft 365, from Exchange to SharePoint.
.png)
Published on
Sep 4, 2025
The Cloudflare Breach: Why Supply Chain Security Can't Be an Afterthought in 2025
The Cloudflare breach is the latest reminder: your supply chain is your attack surface.
.png)
Published on
Sep 3, 2025
The xAI Wake-Up Call: A CISO's Guide to Preventing Data Exfiltration
Insiders have the ultimate exploit: legitimacy. That’s why insider threats are so dangerous. They look normal. Until it’s too late.
.png)
Published on
Aug 29, 2025
Securing Shadow AI: 6 Principles from Security Leaders Who've Been There
Safe AI adoption isn’t about restriction. It’s about visibility, guidance, and smart governance.

Published on
Aug 20, 2025
The Workday Breach: Why Your DLP Strategy Is Already Obsolete
Workday disclosed a breach that exposed customer data through a sophisticated ShinyHunters campaign. Read why this isn’t just another incident: it's proof that traditional DLP is obsolete.

Published on
Aug 13, 2025
Nightfall Product Updates & News: July/August 2025
See Nightfall's new AI-driven features and platform enhancements designed to make your DLP workflows smarter, faster, and more precise.
.png)
Published on
Aug 7, 2025
Designing an Agentic AI Copilot: 8 Principles from Building Nyx
While building Nyx, Nightfall's agentic AI copilot for security teams, our team spent a lot of time thinking about how to make her an effective team member. These are the 8 principles that guided us.
.png)
Published on
Jul 24, 2025
The Nightfall Approach: 5 Ways Our Shadow AI Coverage Differs from Generic DLP
Everyone’s talking about Shadow AI risk. But not all coverage is created equal
.png)
Published on
Jul 17, 2025
Data Flow: Why Most Organizations Don’t Understand Their Information Movement
If you don’t know where your data goes, you can’t protect it.

Published on
Jul 9, 2025
How LLMs Are Changing DLP, And Why That’s a Good Thing
AI is transforming data loss prevention. Here’s why that matters for your security team.
.png)
Published on
Jul 2, 2025
Build vs. Buy: How AI is Shaping Your Next DLP Decision
As AI reshapes the security landscape, every security leader faces a critical question: Should you build your own DLP tools, or buy solutions already powered by AI?

Published on
Jun 24, 2025
Nightfall Product Updates & News: May/June 2025
Product news and updates from Nightfall: improved dashboard, new detectors, and a lot more.

Published on
Jun 18, 2025
From Code to Conversations: How Modern AI Creates New Classes of Data Risk
Chasing AI productivity gains can come with a hidden cost: invisible data exposure
.png)
Published on
May 27, 2025
Now Available: AI-Powered Data Loss Prevention for Microsoft Exchange Online
The Reality Behind Exchange Online DLP: What Customers Actually Experience
.png)
Published on
May 22, 2025
The Missing Layer: Email Protection That Exchange Online and Gmail Users Urgently Need
Go beyond legacy DLP tools to get comprehensive email protection
.png)
Published on
May 15, 2025
Beyond Attachments: How Email Becomes Your Biggest Data Exfiltration Vector
Email has become one of the most notorious data exfiltration vectors
.png)
Published on
May 13, 2025
Enabling Safe AI Adoption: Insights from Nightfall AI and Vanta
A discussion with Rohan Sathe, Co-founder of Nightfall AI, and Unni Patel, Senior Product Manager at Vanta

Published on
May 2, 2025
Nightfall’s Spring 2025 Product Launch Brings DLP to the AI Era
Nightfall's Approach: Enabling secure AI adoption

Published on
Apr 23, 2025
Why Partial DLP Coverage Leaves Your Data Exposed – And How to Fix It
“We have a DLP tool, but we still had no idea this much data was exposed.”
.png)
Published on
Apr 17, 2025
Building DLP for a ChatGPT World
Legacy DLP wasn’t built to protect data from gen AI use
.png)
Published on
Apr 8, 2025
Nightfall Product Updates & News: April 2025
Nightfall Product Updates & News: April 2025

Published on
Apr 3, 2025
G2 Recognizes Nightfall as Data Loss Prevention (DLP) Leader for Spring 2025
G2 Recognizes Nightfall as Data Loss Prevention (DLP) Leader for Spring 2025

Published on
Apr 3, 2025
Secure API Keys and Passwords with Nightfall’s AI-Native DLP
Secure APIs and Passwords with Nightfall’s AI-Native DLP
.png)
Published on
Mar 26, 2025
Insider Risk with Nightfall DLP: Episode 2 - Managing Shadow AI
Nightfall DLP makes it easy to enforce policies to combat shadow AI and keep critical data safe

Published on
Mar 25, 2025
The Essential DLP Checklist for Digital Health and Life Sciences
Protect PHI and PII with Nightfall's Essential DLP Checklist for Health Tech and Life Sciences

Published on
Mar 19, 2025
Why the Future of DLP Is Invisible, Invincible, and Inexpensive
See how the 3 I’s of DLP are built into everything Nightfall does when protecting sensitive data across endpoints and SaaS

Published on
Mar 13, 2025
Insider Risk with Nightfall DLP: Episode 1 - Prevent Personal Cloud Store Uploads
Insider risk illustrated, with Nightfall DLP

Published on
Feb 10, 2025
How to Prevent Sensitive Data Exposure to AI Chatbots Like DeepSeek
Three simple DLP strategies can prevent sensitive data from getting exposed to AI chatbots like DeepSeek

Published on
Feb 5, 2025
Nightfall Releases the 2025 State of Secrets Exposure Report
This year's report offers a look at what changed, what stayed the same, and where you can find a little hope in the quest for effective secrets management.

Published on
Feb 4, 2025
What is Data Lineage and Why Does it Matter in Data Loss Prevention?
Discover what data lineage is and why combining data lineage with AI-driven classification is critical for modern DLP strategies. Learn how tracking data's origin and movement while accurately identifying sensitive content prevents leaks in SaaS, AI, and cloud environments.

Published on
Jan 20, 2025
Here’s What We Can Learn from the Cyberhaven Incident
In December 2024, Cyberhaven fell victim to a sophisticated cyberattack that exploited a phishing campaign targeting its Chrome Web Store account. This breach compromised over 400,000 users by injecting malicious code into its browser extension, exfiltrating sensitive data such as cookies and session tokens. The incident ...

Published on
Jan 14, 2025
Safetica DLP: Comprehensive Analysis & Top Alternatives in 2025
In-depth Safetica DLP guide: explore features, real-world limitations, and how it compares to modern solutions like Nightfall AI for GenAI and cloud data security.

Published on
Jan 8, 2025
CrowdStrike DLP: Comprehensive Review & Top Alternatives in 2025
In-depth 2025 CrowdStrike DLP guide: explore features, real-world limitations, and how it compares to modern solutions like Nightfall AI for GenAI and cloud data security.

Published on
Jan 6, 2025
Code42 Incydr: The Essential Analysis with 50+ FAQs and Top Alternatives
Code42 Incydr is among the legacy solutions aiming to mitigate insider threats, yet it doesn’t always meet every organization’s needs. In the following article, we examine Code42’s capabilities and limitations through a 60-question FAQ that addresses everything you'd want to know when evaluating DLP and IRM solutions.

Published on
Jan 6, 2025
Forcepoint DLP: Comprehensive Review and Top Alternatives in 2025
Discover Forcepoint DLP’s features, limitations, and top alternatives. Learn how AI-driven solutions like Nightfall can protect data more effectively.

Published on
Jan 5, 2025
Symantec DLP: Comprehensive Review and Top Alternatives in 2025
Discover Symantec DLP’s features, limitations, and top alternatives. Learn how AI-driven solutions like Nightfall can protect data more effectively.

Published on
Jan 2, 2025
The 12 Best Data Loss Prevention Software Solutions of 2025 and 50+ FAQs Answered
Learn more about the top 12 best data loss prevention software solutions that can help you protect sensitive data and address 50+ FAQs to guide your evaluation of the top DLP solutions.

Published on
Dec 31, 2024
The 7 Most Telling Data Breaches of 2024
Get the skinny on which 2024 breaches signal the biggest data security threats, trends, and shifts.

Published on
Dec 12, 2024
People Problem or Data Problem? Risks and Mitigation of Insider Threats
What are insider threats, and how can you defend against them?

Published on
Dec 10, 2024
Understanding the Limitations of Atlassian Guard DLP: What You Need to Know
Atlassian collaboration apps enable tremendous productivity, but the way most teams use them poses great risks to your data. Should you use native Atlassian DLP, or look to external cloud DLP to mitigate those risks? Take a deep dive into functionality, advantages, disadvantages, and more to find the right solution for your needs.

Published on
Nov 26, 2024
Loose AWS API keys: what's your real risk?
While malicious actors can gain access to systems in any number of ways, using your API key is the equivalent of walking through a wide-open door and walking in unchecked. Whoever holds that key will have direct access to what are likely your most valuable digital assets.

Published on
Nov 4, 2024
Intelligent Data Classification: Transforming Google Drive Security
Customers need an automated, dynamic, and human-centric cloud DLP solution to label and classify data in Google Drive.

Published on
Oct 28, 2024
How To Prevent Secrets Sprawl
Where are your credentials and secrets, and how are you protecting them?

Published on
Oct 21, 2024
DLP 101: How to Prevent Data Exfiltration in the Cloud
What is data exfiltration, and how can cloud Data Loss Prevention (DLP) help defend against it?

Published on
Sep 30, 2024
10 Essential Guidelines For Enterprise-Ready AI Solutions
AI-powered solutions are becoming increasingly prevalent in enterprise environments, leading to a new trend in procurement: the need for comprehensive AI governance frameworks.

Published on
Sep 24, 2024
Nightfall Named A Leader in Data Loss Prevention by G2
Nightfall leads the way in Data Loss Prevention Software, Data Security Software, and Sensitive Data Discovery Software.

Published on
Sep 18, 2024
Nightfall AI Honored as Winner of the 2024 SC Awards
Nightfall has been recognized in the Best Data Security Solution and Best Insider Threat Solution categories.

Published on
Sep 6, 2024
5 Steps to Send An Encrypted Email in Gmail
Discover how to send encrypted emails in Gmail using Nightfall’s AI-powered encryption tools.

Published on
Sep 4, 2024
Prompt Sanitization: 5 Steps for Protecting Data Privacy in AI Apps
Content filtering and prompt sanitization are key for maintaining security and trust in LLM apps.

Published on
Aug 30, 2024
Nightfall AI selected as 2024 SC Awards Finalist
Nightfall AI has been recognized as a 2024 SC Award finalist in the Trust Award categories for Best Data Security Solution and Best Insider Threat Solution.

Published on
Aug 7, 2024
DLP 101: What is data loss prevention, and why do you need it?
Learn how you can leverage data loss prevention products for continuous data security and compliance.

Published on
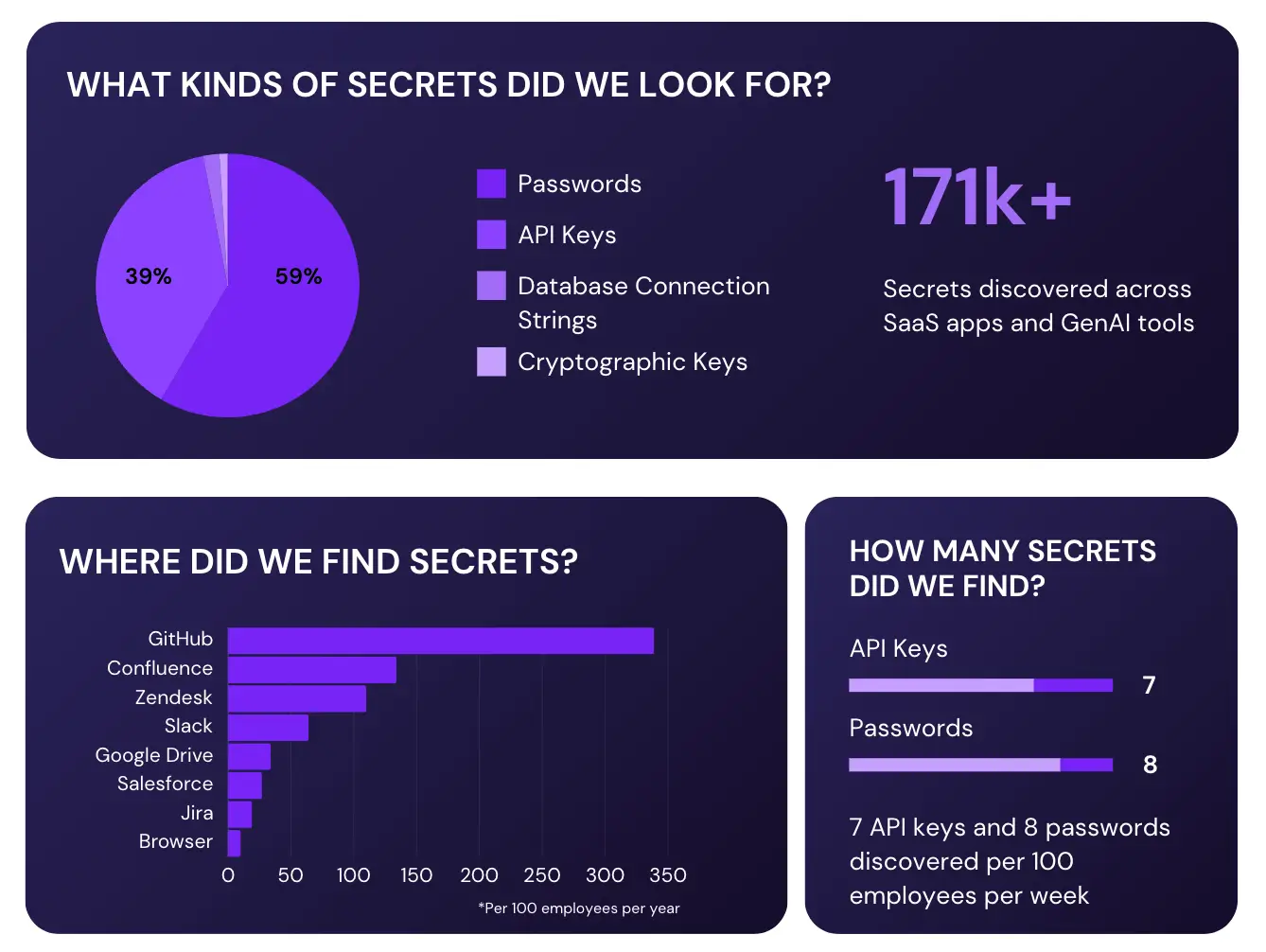
Aug 6, 2024
2024 State of Secrets Report
Do you know where your most sensitive secrets are shared across the cloud? Based on Nightfall’s latest report, odds are that some of them have slipped through the cracks.

Published on
Aug 3, 2024
How to Send Encrypted Emails in Gmail in 5 Easy Steps
Discover how to send encrypted emails in Gmail using Nightfall’s AI-powered encryption tools.

Published on
Aug 1, 2024
Let's chat at Black Hat!
Excited for Black Hat? So are we. Let's meet! We'd love to meet with you to learn more about your data security pain points and share a bit more about our AI-powered solution.

Published on
Jul 17, 2024
Key Learnings from the Disney Breach: 5 Ways to Stop Secret Sprawl
The Disney breach is a wake-up call for any organization that may have secrets sprawled across their tech stack.

Published on
Jul 8, 2024
8 Best Data Leak Prevention (DLP) Policies for Protecting Your Sensitive Data
These popular DLP policies are useful tools for protecting your sensitive data, preventing data exfiltration, securing your AI usage, and more.

Published on
Jul 2, 2024
Nightfall Named A Leader in Data Loss Prevention (DLP) by G2
Nightfall leads the way in G2’s Summer ‘24 reports.

Published on
May 24, 2024
Employee Spotlight: Amit Nene, Engineering Leader
Meet the newest addition to the engineering team at Nightfall AI.

Published on
May 22, 2024
Secure Your AI apps and data pipelines with Nightfall’s Firewall for AI
Nightfall’s Firewall for AI acts as a trust boundary that protects sensitive company and customer data during every stage of AI model building and consumption.

Published on
May 21, 2024
Is Slack using your data to train their AI models? Here’s what you need to know.
With Slack’s AI training policy in the spotlight, it’s time to consider how you can take security for AI into your own hands.

Published on
May 14, 2024
Building your own AI app? Here are 3 risks you need to know about—and how to mitigate them.
From training to annotation to fine-tuning and beyond, here’s how a firewall for AI can help you stay secure as you build your AI model.

Published on
May 13, 2024
5 things you need to know to build a firewall for AI
As organizations expand their use of AI apps, it's important to have a scalable data leak prevention (DLP) solution in place.

Published on
May 6, 2024
4 key takeaways from the 2024 Verizon Data Breach Investigations Report
What are the most common kinds of data breaches—and how can you protect your data against them?

Published on
May 3, 2024
Employee Spotlight: James Jaconetti, VP of Customer Success
Meet the newest addition to the Customer Success team at Nightfall AI.

Published on
May 1, 2024
Top 5 SaaS misconfigurations to avoid and why
It’s essential to be proactive about managing your security posture across SaaS apps like Google Drive and Microsoft OneDrive. Read on to learn why—and how—you can do just that.

Published on
Apr 22, 2024
Here’s what caused the Sisense data breach—and 5 tips for preventing it
Learn what you can do to stop data sprawl and prevent privilege escalation attacks.

Published on
Apr 11, 2024
Nightfall named a “Data Security Solution of the Year”
Nightfall has been named a “Data Security Solution of the Year” by the Data Breakthrough Awards.

Published on
January 29, 2025
Intellectual Property Theft: The Essential Guide
Learn what intellectual property theft is, common types of theft, strategies for protecting IP, and how to respond to IP theft.

Published on
February 3, 2025
Shadow AI: The Essential Guide
Shadow AI has swiftly become one of the most pressing data security risks facing modern enterprises. Learn what shadow AI is and how to combat it.

Published on
January 13, 2025
The Essential Guide to Data Loss Prevention for Financial Services and Fintech
By following these best practices, financial services and fintech companies can build robust DLP strategies that protect sensitive data, maintain regulatory compliance, and preserve customer trust.

Published on
January 10, 2025
The Essential Guide to Data Loss Prevention for Investment Firms
By following these best practices, investment firms can build robust DLP strategies that protect sensitive data, maintain regulatory compliance, and preserve customer trust.

Published on
January 9, 2025
The Essential Guide to Data Loss Prevention for Law Firms
By following these best practices, law firms can build robust DLP strategies that protect sensitive data, maintain regulatory compliance, and preserve customer trust.

Published on
January 8, 2025
The Essential Guide to Data Loss Prevention for Biotech and Pharma
By following these best practices, biotech and pharma companies can build robust DLP strategies that protect sensitive data, maintain regulatory compliance, and preserve customer trust.

Published on
January 7, 2025
The Essential Guide to Data Loss Prevention for Healthcare
By following these best practices, healthcare organizations can build robust DLP strategies that protect sensitive data, maintain regulatory compliance, and preserve customer trust.

Published on
November 1, 2024
The Essential Guide to Data Loss Prevention for Manufacturers
By following these best practices, manufacturers can build robust DLP strategies that protect sensitive data, maintain regulatory compliance, and preserve customer trust.
Published on
February 17, 2025
2025 State of Secrets Exposure Report
Learn what secret types were most exposed last year, where your greatest risks are, associated threats, how collaborative remediation impacts data hygiene, and more.
Published on
2024 State of Secrets Exposure Report
Do you know where your most sensitive secrets are shared across the cloud? Based on Nightfall’s latest report, odds are that some of them have slipped through the cracks.

Published on
June 17, 2024
Navigating Data Privacy for GenAI in Customer Support
As the adoption of generative AI (GenAI) accelerates across enterprises, one of the most promising applications emerges in customer support.

Published on
June 17, 2024
Do You Use These Top SaaS Apps? Here’s what you need to know about Data Sprawl
Nightfall’s recent “State of Secrets” report uncovered that collaboration, communication, and IT service tools have the highest risk of data exposure, particularly in industry-leading SaaS apps like Slack and GitHub.

Published on
June 17, 2024
The Essential Guide to Data Loss Prevention (DLP) for LLMs
SaaS companies can level up their features by leveraging third-party sub-processors from public models like OpenAl and Anthropic.

Published on
June 17, 2024
The Ultimate guide to security for GenAI
From customer service chatbots to enterprise search tools, companies are fervently seeking new ways to leverage both first-party and third-party LLMs to stay on the cutting edge of innovation.

Published on
June 17, 2024
The Ultimate Guide to PCI Security and Compliance
From fintech firms to retail merchants, PCI standards are nearly ubiquitous across many industries.

Published on
December 22, 2023
The Ultimate Guide to Cloud DLP for GenAI
Leverage AI and machine learning for better sensitive data detection.

Published on
October 17, 2023
Cloud DLP (Data Leak Prevention): The Essential Guide
Cloud DLP, or cloud data leak prevention (DLP), is a critical aspect of data security. Here's what you need to know about it.

Published on
August 4, 2023
The Essential Guide to Data Loss Prevention (DLP) for LLMs
Learn how to stay secure while using and building LLMs.

Published on
August 4, 2023
ChatGPT DLP (Data Loss Prevention): The Essential Guide
Learn how to minimize data exposure and maintain compliance while unlocking the benefits of ChatGPT.

Published on
May 8, 2023
Guide To HIPAA Compliance for SaaS Applications
From our security checklist learn the types of questions you should ask SaaS vendors when evaluating how a specific platform fits into your compliance program.

Published on
May 9, 2023
PCI Compliance Checklist for Modern Organizations
This checklist highlights core aspects of PCI compliance and security standards, as well as how to implement them. Read online for free.

Published on
June 7, 2023
The Business Case for Cloud DLP (Data Leak Prevention)
The expanding universe of business-critical cloud applications creates increased risk for the exposure of sensitive data learn how to mitigate this risk.

Published on
May 9, 2023
Slack DLP (Data Loss Prevention): The Essential Guide
Learn how to implement data loss prevention (DLP) on Slack, and detect leakage of sensitive data across any Slack workspace with this free online guide.

Published on
May 9, 2023
The Ultimate HIPAA Security & Compliance FAQ
HIPAA compliance is a complex topic. That’s why we’ve complied the most frequently asked questions with detailed answers.

Published on
May 10, 2023
Salesforce DLP (Data Loss Prevention): The Essential Guide
Read this online guide, for free, to learn about the problem of data exposure in Salesforce and how to ensure compliance with HIPAA, PCI, and more.

Published on
May 9, 2023
Confluence DLP (Data Loss Prevention): The Essential Guide
Read this online guide, for free, to learn how knowledge wikis like Confluence can increase the exposure risk for sensitive data like PHI, PII, and API keys.

Published on
May 9, 2023
DLP APIs (Data Loss Prevention): The Essential Guide
Learn about the growing problem of sensitive data exposure and how to use the Nightfall Developer Platform to easily identify and remediate this problem.

Published on
May 9, 2023
Google Drive DLP (Data Loss Prevention): The Essential Guide
Read this online guide, for free, to learn how large-scale collaboration in tools like Google Drive can increase exposure risk for sensitive data like PHI & PII.

Published on
May 9, 2023
The 2023 Security Playbook for Remote-First Organizations
Learn how to more securely manage your remote workforce to become a true remote-first organization.

Published on
October 22, 2024
6 Steps to Protect Google Drive with Data Loss Prevention
This guide is written to help you illustrate the potential data protection gaps in a deployment of Google Drive to your team and stakeholders.

Published on
May 9, 2023
Slack HIPAA Compliance: The Definitive Guide
Read a free, online overview of HIPAA requirements for covered entities using Slack Workspaces and what's needed to satisfy them.

Published on
May 9, 2023
GitHub DLP (Data Loss Prevention): The Essential Guide
Read this online guide, for free, to learn about the problem of secrets exposure and leakage in GitHub, as well as how to easily implement secrets detection.

Published on
May 9, 2023
Jira DLP (Data Loss Prevention): The Essential Guide
Learn how project management applications like Jira increase the exposure risk for sensitive data like secrets, PII, & more.

Published on
May 9, 2023
Cloud Security Policy Template
In this guide, we’ll break down how to create a cloud security policy and provide a free template to help you get started.

Published on
January 27, 2026
Nightfall Product Launch 2026: Securing AI Agents & the MCP Security Challenge
Detecting and Governing Model Context Protocol (MCP) Connections Is the New Security Frontier

Published on
January 27, 2026
Nightfall Product Launch 2026: Forensic Search & App Intelligence
A New, Faster Approach to Insider Risk Investigations and Gen AI Governance

Published on
January 27, 2026
Nightfall Product Launch 2026: Comprehensive Exfiltration Prevention
Prevent Data Loss Across Gen AI, Browsers, Email, and Source Code with AI-Native Detection

Published on
January 27, 2026
Nightfall Product Launch 2026: AI-Powered Detection & Classification
See how AI-powered detection achieves 95% precision and eliminates false positives

Published on
January 27, 2026
Nightfall Demo: Stop Data Leaks to Personal Accounts with Identity Context
Nightfall Distinguishes Between Corporate and Personal App Usage to Prevent Risky Exfiltration

Published on
January 27, 2026
Nightfall Demo: Build Data Security Policies in Minutes, Not Months
Master Policy-Based Data Protection Across Every Exfiltration Vector

Published on
January 26, 2026
Nightfall Demo: Git Push Monitoring
Prevent Source Code Exfiltration with Real-Time Git Push Monitoring

Published on
January 26, 2026
Nightfall Demo: App Intelligence
App intelligence turns raw endpoint data into actionable insights for safe GenAI adoption

Published on
January 26, 2026
Nightfall Demo: Block Shadow AI Without Compromising on Productivity
Nightfall AI Stops Corporate IP Leaks to Shadow AI Apps

Published on
January 26, 2026
Nightfall Demo: Personal vs. Corporate Session Differentiation
Context-Aware DLP Protects Your Sensitive Data Across Every Endpoint

Published on
January 26, 2026
Nightfall Demo: DLP Forensic Search
Reconstruct Any Insider Risk Investigation for Valuable Insights

Published on
January 26, 2026
Nightfall Demo: Nyx, the AI-Powered SOC Analyst
Transform hours of security investigation into minutes with natural language queries with Nyx

Published on
January 26, 2026
Nightfall Demo: DLP for Removable Media
Removable media remains one of the most challenging exfiltration vectors for security teams. Nightfall DLP makes it easy to protect against data loss through USB devices and more

Published on
January 26, 2026
Nightfall Demo: AI Browser Security
AI Browser Security is the Future of Data Loss Prevention

Published on
January 26, 2026
Nightfall DLP Overview: MCP
Nightfall Delivers Industry-First Visibility and Control for MCP

Published on
January 26, 2026
Nightfall Demo: DLP for Email
Next-Gen Protection Against Email Exfiltration
.png)
Published on
January 20, 2026
Nightfall Product Launch 2026: The Future of Data Loss Prevention
Modern data loss happens faster than policies, alerts, and manual tuning. See what DLP looks like when AI does the heavy lifting.
.png)
Published on
January 12, 2026
Data Exfiltration Prevention: Best Practices with Nightfall AI
A practical look at how security teams detect and stop data exfiltration across AI tools, cloud apps, browsers, and more

Published on
October 10, 2025
Webinar: Unlocking Complete Data Visibility with AI-Native DLP
See how Nightfall empowers SecOps teams to protect sensitive data efficiently and confidently

Published on
September 25, 2025
Webinar: Supercharging SecOps with Automation & AI
Explore how automation and AI are reshaping security operations today. And what leaders must do to strike the right balance between innovation and protection.

Published on
August 21, 2025
A Fireside Chat with Rohan Sathe and Kelvin Beachum, Jr.
Nightfall CEO and co-founder Rohan Sathe chats with NFL vet & tech investor Kelvin Beachum, Jr. on football, AI, and insights from a career in sports and in tech.

Published on
August 21, 2025
Webinar: Designing Trust: Embedding Privacy & Security Into Enterprise AI
Nightfall Head of Product Anant Mahajan and Yunique Demann, CTO TPx. discuss how security leaders enable safe, responsible AI adoption and share insights on AI governance, visibility, and innovation.

Published on
August 21, 2025
Webinar: Enabling AI Adoption with Data Security and Compliance
Rohan Sathe (CEO and Co-Founder, Nightfall AI) and Unni Patel (Senior Product Manager at Vanta) discuss how data security and continuous compliance empower organizations to safely adopt generative AI tools.

Published on
August 21, 2025
Nightfall Demo: Natural Language Detectors
Go beyond regex with Nightfall AI’s custom detectors: create prompt-based rules to detect sensitive data anywhere using natural language.
.png)
Published on
August 21, 2025
Nightfall Demo: Comprehensive AI-Powered DLP for Microsoft 365
Nightfall’s Microsoft 365 DLP uses advanced AI detection and intelligent remediation to protect sensitive data and prevent leaks across SharePoint and Exchange.

Published on
August 21, 2025
Nightfall Demo: A Unique Approach to Endpoint DLP
Nightfall’s endpoint data leak protection supported by data lineage capabilities and full coverage across all major exfiltration vectors.
.png)
Published on
August 8, 2025
Nightfall Demo: Exchange Online
See Nightfall in action and how to keep all your data safe and secure when sending and receiving emails in Exchange Online.

Published on
August 8, 2025
Build vs. Buy: Designing an Effective DLP Program in the AI Era
Nightfall AI's co-founder Rohan Sathe sits down with Confluent CISO Chris Sandulow to share their thoughts on how to choose the right DLP solution for any organization.

Published on
August 8, 2025
Nightfall AI Spring 2025 Product Launch
With our Spring 2025 Product Launch, Nightfall is redefining DLP for the age of generative AI. Learn how to secure data when using any AI apps like ChatGPT, Deepseek, Claude, Gemini and more.

Published on
August 8, 2025
Nightfall Demo: Detect & Remediate Data Exposure in SaaS
Learn how Nightfall detects and remediates sensitive data exposure in SaaS apps like Slack, Google Workspace, Atlassian, Salesforce, Microsoft 365 and more.

Published on
August 8, 2025
Nightfall Demo: Manage Sharing Permissions Settings in SaaS Apps
Manage external sharing risks in SaaS apps like Google Drive and Slack with real-time alerts, automated remediation, and data lineage.

Published on
August 8, 2025
Nightfall Demo: DLP for Gmail
Native Gmail integration scans emails inline and allows users to set up custom policies to block, quarantine, redact, and encrypt emails for a full range of email security options.

Published on
August 8, 2025
Nightfall Demo: Secure Data When Using Gen AI Tools & Chatbots
Nightfall’s endpoint agent and browser plugin keeps your data safe across AI apps. See the power of gaining full visibility and context through data lineage.

Published on
August 8, 2025
Nightfall Demo: Protecting Data in Endpoints and Browsers with AI
Nightfall prevents data exfiltration for endpoints and browsers with AI-native DLP that’s lightweight and seamless to integrate into all your systems.

Published on
August 7, 2025
Eclipse - Nyx Copilot
Meet Nyx, Nightfall’s new agentic AI copilot for DLP. Nyx works like a teammate: she understands context, acts safely, and simplifies complex workflows.
.png)
Published on
August 7, 2025
Eclipse - A Unique Approach to Endpoint DLP
See Nightfall in action in this live demonstration of our latest data lineage capabilities and comprehensive coverage across all major exfiltration vectors.

Published on
August 7, 2025
Eclipse - Comprehensive AI-Powered DLP for Microsoft 365
See how to protect data across Microsoft Sharepoint and Exchange with Nightfall’s comprehensive M365 DLP featuring advanced AI detection and smart remediation.

Published on
August 7, 2025
Eclipse - Opening Keynote: Key Product Announcements
Nightfall co-founder and CEO Rohan Sathe shares an exclusive first look at Nightfall's latest breakthrough innovations in AI-powered DLP.

Published on
August 7, 2025
Eclipse - A Fireside Chat with Rohan Sathe & Enrique Salem
Nightfall co-founder Rohan Sathe and Enrique Salem, Partner at BCV, discuss the future of AI-powered data loss prevention from builder and investor perspectives.

Published on
August 7, 2025
Eclipse - Secure AI Adoption: Preventing Leakage in Shadow AI Applications
Learn how to implement visibility and controls that prevent sensitive data leakage to AI applications without blocking productivity with Nightfall DLP.

Published on
July 1, 2024
3 Ways to Prevent Data Exfiltration in your SaaS Apps
Data exfiltration poses a significant threat to organizations across all industries. With cybercriminals using increasingly sophisticated methods to illicitly obtain sensitive information, IT and security teams face the daunting task of protecting their digital assets against both internal and external threats. This webinar will provide your team some practical strategies to enhance your company's defenses against data exfiltration.

Published on
May 20, 2024
Protect Your Email From Sensitive Data Loss and Data Exfiltration
Email remains a critical channel for business communication and also remains a prime exfiltration and attack vector. Traditional Secure Email Gateways (SEGs) and rules-based DLP solutions are proving inadequate against data loss, exfiltration, sophisticated attacks and the complexities of modern cloud environments. Whether your organization relies on Gmail or Exchange or a hybrid email environment, Nightfall AI can protect your email against data loss and exfiltration with a comprehensive, flexible, and efficient approach to protecting your email across platforms.

Published on
December 6, 2023
Building Security at an Enterprise Scale
Nightfall for Notion DLP is purpose-built to pinpoint sensitive data across Notion workspaces. Whether you’re using Notion as an internal wiki, a note-taking app, or something more, Nightfall’s AI-powered detectors will identify and remediate high-priority risks to ensure that your business stays continuously secure and compliant as you scale.

Published on
November 28, 2023
Next-Gen Secrets Detection for the Age of AI
All employees have a part to play in keeping company secrets safe—however, developers have an outsized role due to their privileged access to sensitive databases, production systems, and source code. With these unique challenges in mind, Nightfall partnered with Snyk to offer AI-powered secrets scanning for developers working in every stage of the code-to-cloud lifecycle.

Published on
August 1, 2023
ChatGPT and Gen AI: How to Stay Secure and Compliant
Generative AI is exploding, allowing companies to do more with less. It is, however, also exposing companies to more data security risks than ever before. In our upcoming fireside chat, we'll join Enrique Salem, former CEO of Symantec, and Isaac Madan, CEO of Nightfall, to discuss the biggest security risks of Gen AI, as well as strategies you need to stay compliant without impacting employee innovation. By the end of the chat, you'll be armed with the tools you need to safely use ChatGPT and other Gen AI tools across your business. See you there!

Published on
July 10, 2023
How Security and Compliance Can Help Unlock Enterprise Customers
Security is of paramount importance for organizations trying to shorten their sales cycles and unlock enterprise clients. Learn how to use security as a differentiator in today’s challenging macroeconomic climate.

Published on
June 14, 2022
Build Continuous Security & Compliance into Your SaaS Environments
As recent trends, like supply chain attacks and cloud data leaks have made clear, continuous security and continuous data compliance must be embedded into the application, no matter where it is deployed, and who is accessing it.

Published on
June 8, 2021
Learn How to Protect Codebases from Secrets Exfiltration
Listen to Nightfall’s CTO, Rohan Sathe, and product specialist, Michael Osakwe, to learn about the increased exfiltration risks posed by code repositories. Learn how threat actors are incorporating targets like GitHub into their attacks, why this has become more common, and best practices to reduce your attack surface.

Published on
June 14, 2022
Enhance Data Governance & Intelligence across SaaS Systems
Enterprise legal, compliance, and governance teams struggle to detect, manage, govern, and protect information in near real time. Similarly, litigation, HR and investigation teams struggle with data intelligence on information they have collected from cloud applications like Slack and Google Workspace.

Published on
November 22, 2021
Learn How Bluecore Maintains Data Security on Slack with Nightfall
SaaS applications like Slack are challenging environments for enforcing data security policies. This is especially true for innovative, high-growth companies that have embraced a cloud-first philosophy.

Published on
April 28, 2021
Data Classification & Protection with the Nightfall Developer Platform
A myriad of organizations rely on Nightfall, the industry’s first cloud-native data loss prevention (DLP) solution, to implement DLP into essential cloud applications like Slack, GitHub, and Google Drive.

Published on
August 24, 2020
HIPAA Compliance Requirements & Best Practices for Slack
It's important that HIPAA covered entities interested in Slack understand what's needed to ensure they remain compliant while using the platform.

Published on
April 8, 2020
How to Discover & Protect Sensitive Data in Slack
Collaborative SaaS applications like Slack create environments where data policy and security best practices are difficult to maintain or enforce without an excessive time or resource commitment.

Published on
March 2, 2021
How to Identify & Protect Sensitive Data in AWS
Some of the biggest data leaks in history have occurred due to problems with Amazon Web Services (AWS S3), like permissions misconfigurations, secrets mismanagement, improper security configurations, or maintaining a poor visibility environment.

Published on
March 2, 2021
Securing Best of Breed SaaS Applications in 2021
The explosive growth of SaaS collaboration tools and other cloud-based platforms makes it paramount that organizations understand how to secure data in the cloud
Published on
March 2, 2021
Discover Secrets Leaks in Code Repos with Nightfall for GitHub
Git-based repositories can create environments where secrets & credentials are exposed without notice, especially in environments with lots of contributors and few guidelines regarding best practices for handling credentials or environments with external collaborators who might not be familiar with best practices

Published on
Protected Health Information (PHI) detector for digital healthcare datasheet
Healthcare organizations require an effective way to scale HIPAA compliance enforcement across their cloud applications without excessive time and resource commitment. This requires a high-accuracy solution capable of parsing context to identify PHI violations as they are defined by HIPAA

Published on
Nightfall Advanced Secrets Detection Datasheet
Exposure of secrets like API keys is a common problem that can lead to privilege escalation of security incidents if accessed by malicious actors. Addressing this problem requires a solution tuned to detect secrets in any format, wherever they are.

Published on
PCI Compliance Checklist for Modern Organizations
This checklist highlights core aspects of PCI compliance and security standards, as well as how to implement them.

Published on
Cloud Security Policy Template
Protecting your data in the cloud starts with developing a cloud security policy to govern user access, meet compliance standards, secure data in use, and maintain defenses against cyber threats.

Published on
Guide to Data Loss Prevention (DLP) for Jira
Data loss prevention (DLP) is an important part of data security and compliance in the cloud, especially for organizations using SaaS applications that store high volumes of data. Companies turn to DLP solutions to discover, classify, and protect their sensitive data in environments like Jira, and maintain compliance with regimes like GDPR, CCPA, PCI, and more.

Published on
Guide to Data Loss Prevention (DLP) for Github
Learn how to detect the leakage of secrets, credentials, and other sensitive data across your code repositories with this brief guide.

Published on
Guide to HIPAA Compliance on Slack
Data loss prevention (DLP) is an important part of data security and compliance in the cloud, especially for organizations regulated by HIPAA. Furthermore, healthcare teams using Slack must follow specific guidelines laid out in Slack’s Business Associate Agreement (BAA).

Published on
6 Steps to Protect Google Drive with Data Loss Protection
Google Drive is core to enabling collaboration and access to business-critical files, but it is difficult to audit which files within Google Drive have sensitive information and who has access to them.

Published on
The 2023 Security Playbook for Remote-First Organizations
Learn how to more securely manage your remote workforce to become a true remote-first organization.

Published on
Guide to Data Loss Prevention (DLP) in Google Drive
Data loss prevention (DLP) is an important part of data security and compliance in the cloud, especially for organizations using SaaS applications that store high volumes of data. Companies turn to DLP solutions to discover, classify, and protect their sensitive data in environments like Google Drive, and maintain compliance with regimes like GDPR, CCPA, PCI, and more.

Published on
Data Security with the Nightfall Developer Platform
As a result of growing data breaches governments across the world are beginning to implement compliance regimes which require organizations to understand the quantity and nature of that data they’re ingesting. The Nightfall developer platform is designed to help organizations accomplish this with APIs that allow developers to stream data to our machine learning detectors for classification.

Published on
Guide to Data Loss Prevention (DLP) for Confluence
Learn how to detect the leakage of secrets and other business-critical data within Atlassian Confluence

Published on
Guide To HIPAA Compliance for SaaS Applications
SaaS applications enable healthcare organizations to leverage digital transformation to improve healthcare outcomes and change lives, but ensuring your organization remains compliant while adopting cloud applications can prove challanging.

Published on
The Business Case for Cloud Data Protection
As organizations continue to rapidly adopt SaaS and cloud infrastructure, IT and security teams are becoming stretched. The expanding universe of business-critical cloud applications creates increased risk for the exposure of sensitive data like PII, PHI, as well as secrets and credentials. Cloud data protection is essential to ensuring employees follow best practices for handling sensitive data and that systems are configured in a manner that prevents unauthorized access.

Published on
Guide To Data Loss Prevention (DLP) for Salesforce
Learn how to discover and prevent the leakage of customer information and other business-critical data within Salesforce

Published on
HIPAA Security Rule Implementation Specification Matrix
In order to fulfill the HIPAA Security Rule, covered entities and business associates must evaluate the implementation specifications or requirements listed under each Security Rule Safeguard in order to determine how best satisfy each. We’ve built out a matrix to explain each individual HIPAA Security Rule requirement in plain English.

Published on
The Ultimate HIPAA Security & Compliance FAQ
HIPAA compliance is a complex topic. That’s why we’ve complied the most frequently asked questions with detailed answers to help guide you through the compliance process.

Published on
Guide to Data Loss Prevention (DLP) for Slack
Data loss prevention (DLP) is an important part of data security and compliance in the cloud. Companies turn to DLP solutions to discover, classify, and protect their sensitive data in collaborative environments like Slack, and maintain compliance with regimes like HIPAA, GDPR, CCPA, PCI, and more.

Published on
January 29, 2025
Intellectual Property Theft: The Essential Guide
Learn what intellectual property theft is, common types of theft, strategies for protecting IP, and how to respond to IP theft.

Published on
February 3, 2025
Shadow AI: The Essential Guide
Shadow AI has swiftly become one of the most pressing data security risks facing modern enterprises. Learn what shadow AI is and how to combat it.

Published on
January 13, 2025
The Essential Guide to Data Loss Prevention for Financial Services and Fintech
By following these best practices, financial services and fintech companies can build robust DLP strategies that protect sensitive data, maintain regulatory compliance, and preserve customer trust.

Published on
January 10, 2025
The Essential Guide to Data Loss Prevention for Investment Firms
By following these best practices, investment firms can build robust DLP strategies that protect sensitive data, maintain regulatory compliance, and preserve customer trust.

Published on
January 9, 2025
The Essential Guide to Data Loss Prevention for Law Firms
By following these best practices, law firms can build robust DLP strategies that protect sensitive data, maintain regulatory compliance, and preserve customer trust.

Published on
January 8, 2025
The Essential Guide to Data Loss Prevention for Biotech and Pharma
By following these best practices, biotech and pharma companies can build robust DLP strategies that protect sensitive data, maintain regulatory compliance, and preserve customer trust.

Published on
January 7, 2025
The Essential Guide to Data Loss Prevention for Healthcare
By following these best practices, healthcare organizations can build robust DLP strategies that protect sensitive data, maintain regulatory compliance, and preserve customer trust.

Published on
November 1, 2024
The Essential Guide to Data Loss Prevention for Manufacturers
By following these best practices, manufacturers can build robust DLP strategies that protect sensitive data, maintain regulatory compliance, and preserve customer trust.

Published on
February 17, 2025
2025 State of Secrets Exposure Report
Learn what secret types were most exposed last year, where your greatest risks are, associated threats, how collaborative remediation impacts data hygiene, and more.

Published on
2024 State of Secrets Exposure Report
Do you know where your most sensitive secrets are shared across the cloud? Based on Nightfall’s latest report, odds are that some of them have slipped through the cracks.

Published on
June 17, 2024
Navigating Data Privacy for GenAI in Customer Support
As the adoption of generative AI (GenAI) accelerates across enterprises, one of the most promising applications emerges in customer support.

Published on
June 17, 2024
Do You Use These Top SaaS Apps? Here’s what you need to know about Data Sprawl
Nightfall’s recent “State of Secrets” report uncovered that collaboration, communication, and IT service tools have the highest risk of data exposure, particularly in industry-leading SaaS apps like Slack and GitHub.

Published on
June 17, 2024
The Essential Guide to Data Loss Prevention (DLP) for LLMs
SaaS companies can level up their features by leveraging third-party sub-processors from public models like OpenAl and Anthropic.

Published on
June 17, 2024
The Ultimate guide to security for GenAI
From customer service chatbots to enterprise search tools, companies are fervently seeking new ways to leverage both first-party and third-party LLMs to stay on the cutting edge of innovation.

Published on
June 17, 2024
The Ultimate Guide to PCI Security and Compliance
From fintech firms to retail merchants, PCI standards are nearly ubiquitous across many industries.

Published on
December 22, 2023
The Ultimate Guide to Cloud DLP for GenAI
Leverage AI and machine learning for better sensitive data detection.

Published on
October 17, 2023
Cloud DLP (Data Leak Prevention): The Essential Guide
Cloud DLP, or cloud data leak prevention (DLP), is a critical aspect of data security. Here's what you need to know about it.

Published on
August 4, 2023
The Essential Guide to Data Loss Prevention (DLP) for LLMs
Learn how to stay secure while using and building LLMs.

Published on
August 4, 2023
ChatGPT DLP (Data Loss Prevention): The Essential Guide
Learn how to minimize data exposure and maintain compliance while unlocking the benefits of ChatGPT.

Published on
May 8, 2023
Guide To HIPAA Compliance for SaaS Applications
From our security checklist learn the types of questions you should ask SaaS vendors when evaluating how a specific platform fits into your compliance program.

Published on
May 9, 2023
PCI Compliance Checklist for Modern Organizations
This checklist highlights core aspects of PCI compliance and security standards, as well as how to implement them. Read online for free.

Published on
June 7, 2023
The Business Case for Cloud DLP (Data Leak Prevention)
The expanding universe of business-critical cloud applications creates increased risk for the exposure of sensitive data learn how to mitigate this risk.

Published on
May 9, 2023
Slack DLP (Data Loss Prevention): The Essential Guide
Learn how to implement data loss prevention (DLP) on Slack, and detect leakage of sensitive data across any Slack workspace with this free online guide.

Published on
May 9, 2023
The Ultimate HIPAA Security & Compliance FAQ
HIPAA compliance is a complex topic. That’s why we’ve complied the most frequently asked questions with detailed answers.

Published on
May 10, 2023
Salesforce DLP (Data Loss Prevention): The Essential Guide
Read this online guide, for free, to learn about the problem of data exposure in Salesforce and how to ensure compliance with HIPAA, PCI, and more.

Published on
May 9, 2023
Confluence DLP (Data Loss Prevention): The Essential Guide
Read this online guide, for free, to learn how knowledge wikis like Confluence can increase the exposure risk for sensitive data like PHI, PII, and API keys.

Published on
May 9, 2023
DLP APIs (Data Loss Prevention): The Essential Guide
Learn about the growing problem of sensitive data exposure and how to use the Nightfall Developer Platform to easily identify and remediate this problem.

Published on
May 9, 2023
Google Drive DLP (Data Loss Prevention): The Essential Guide
Read this online guide, for free, to learn how large-scale collaboration in tools like Google Drive can increase exposure risk for sensitive data like PHI & PII.

Published on
May 9, 2023
The 2023 Security Playbook for Remote-First Organizations
Learn how to more securely manage your remote workforce to become a true remote-first organization.

Published on
October 22, 2024
6 Steps to Protect Google Drive with Data Loss Prevention
This guide is written to help you illustrate the potential data protection gaps in a deployment of Google Drive to your team and stakeholders.

Published on
May 9, 2023
Slack HIPAA Compliance: The Definitive Guide
Read a free, online overview of HIPAA requirements for covered entities using Slack Workspaces and what's needed to satisfy them.

Published on
May 9, 2023
GitHub DLP (Data Loss Prevention): The Essential Guide
Read this online guide, for free, to learn about the problem of secrets exposure and leakage in GitHub, as well as how to easily implement secrets detection.

Published on
May 9, 2023
Jira DLP (Data Loss Prevention): The Essential Guide
Learn how project management applications like Jira increase the exposure risk for sensitive data like secrets, PII, & more.

Published on
May 9, 2023
Cloud Security Policy Template
In this guide, we’ll break down how to create a cloud security policy and provide a free template to help you get started.

Published on
January 27, 2026
Nightfall Product Launch 2026: Securing AI Agents & the MCP Security Challenge
Detecting and Governing Model Context Protocol (MCP) Connections Is the New Security Frontier

Published on
January 27, 2026
Nightfall Product Launch 2026: Forensic Search & App Intelligence
A New, Faster Approach to Insider Risk Investigations and Gen AI Governance

Published on
January 27, 2026
Nightfall Product Launch 2026: Comprehensive Exfiltration Prevention
Prevent Data Loss Across Gen AI, Browsers, Email, and Source Code with AI-Native Detection

Published on
January 27, 2026
Nightfall Product Launch 2026: AI-Powered Detection & Classification
See how AI-powered detection achieves 95% precision and eliminates false positives

Published on
January 27, 2026
Nightfall Demo: Stop Data Leaks to Personal Accounts with Identity Context
Nightfall Distinguishes Between Corporate and Personal App Usage to Prevent Risky Exfiltration

Published on
January 27, 2026
Nightfall Demo: Build Data Security Policies in Minutes, Not Months
Master Policy-Based Data Protection Across Every Exfiltration Vector

Published on
January 26, 2026
Nightfall Demo: Git Push Monitoring
Prevent Source Code Exfiltration with Real-Time Git Push Monitoring

Published on
January 26, 2026
Nightfall Demo: App Intelligence
App intelligence turns raw endpoint data into actionable insights for safe GenAI adoption

Published on
January 26, 2026
Nightfall Demo: Block Shadow AI Without Compromising on Productivity
Nightfall AI Stops Corporate IP Leaks to Shadow AI Apps

Published on
January 26, 2026
Nightfall Demo: Personal vs. Corporate Session Differentiation
Context-Aware DLP Protects Your Sensitive Data Across Every Endpoint

Published on
January 26, 2026
Nightfall Demo: DLP Forensic Search
Reconstruct Any Insider Risk Investigation for Valuable Insights

Published on
January 26, 2026
Nightfall Demo: Nyx, the AI-Powered SOC Analyst
Transform hours of security investigation into minutes with natural language queries with Nyx

Published on
January 26, 2026
Nightfall Demo: DLP for Removable Media
Removable media remains one of the most challenging exfiltration vectors for security teams. Nightfall DLP makes it easy to protect against data loss through USB devices and more

Published on
January 26, 2026
Nightfall Demo: AI Browser Security
AI Browser Security is the Future of Data Loss Prevention

Published on
January 26, 2026
Nightfall DLP Overview: MCP
Nightfall Delivers Industry-First Visibility and Control for MCP

Published on
January 26, 2026
Nightfall Demo: DLP for Email
Next-Gen Protection Against Email Exfiltration
.png)
Published on
January 20, 2026
Nightfall Product Launch 2026: The Future of Data Loss Prevention
Modern data loss happens faster than policies, alerts, and manual tuning. See what DLP looks like when AI does the heavy lifting.
.png)
Published on
January 12, 2026
Data Exfiltration Prevention: Best Practices with Nightfall AI
A practical look at how security teams detect and stop data exfiltration across AI tools, cloud apps, browsers, and more

Published on
October 10, 2025
Webinar: Unlocking Complete Data Visibility with AI-Native DLP
See how Nightfall empowers SecOps teams to protect sensitive data efficiently and confidently

Published on
September 25, 2025
Webinar: Supercharging SecOps with Automation & AI
Explore how automation and AI are reshaping security operations today. And what leaders must do to strike the right balance between innovation and protection.

Published on
August 21, 2025
A Fireside Chat with Rohan Sathe and Kelvin Beachum, Jr.
Nightfall CEO and co-founder Rohan Sathe chats with NFL vet & tech investor Kelvin Beachum, Jr. on football, AI, and insights from a career in sports and in tech.

Published on
August 21, 2025
Webinar: Designing Trust: Embedding Privacy & Security Into Enterprise AI
Nightfall Head of Product Anant Mahajan and Yunique Demann, CTO TPx. discuss how security leaders enable safe, responsible AI adoption and share insights on AI governance, visibility, and innovation.

Published on
August 21, 2025
Webinar: Enabling AI Adoption with Data Security and Compliance
Rohan Sathe (CEO and Co-Founder, Nightfall AI) and Unni Patel (Senior Product Manager at Vanta) discuss how data security and continuous compliance empower organizations to safely adopt generative AI tools.

Published on
August 21, 2025
Nightfall Demo: Natural Language Detectors
Go beyond regex with Nightfall AI’s custom detectors: create prompt-based rules to detect sensitive data anywhere using natural language.
.png)
Published on
August 21, 2025
Nightfall Demo: Comprehensive AI-Powered DLP for Microsoft 365
Nightfall’s Microsoft 365 DLP uses advanced AI detection and intelligent remediation to protect sensitive data and prevent leaks across SharePoint and Exchange.

Published on
August 21, 2025
Nightfall Demo: A Unique Approach to Endpoint DLP
Nightfall’s endpoint data leak protection supported by data lineage capabilities and full coverage across all major exfiltration vectors.
.png)
Published on
August 8, 2025
Nightfall Demo: Exchange Online
See Nightfall in action and how to keep all your data safe and secure when sending and receiving emails in Exchange Online.

Published on
August 8, 2025
Build vs. Buy: Designing an Effective DLP Program in the AI Era
Nightfall AI's co-founder Rohan Sathe sits down with Confluent CISO Chris Sandulow to share their thoughts on how to choose the right DLP solution for any organization.

Published on
August 8, 2025
Nightfall AI Spring 2025 Product Launch
With our Spring 2025 Product Launch, Nightfall is redefining DLP for the age of generative AI. Learn how to secure data when using any AI apps like ChatGPT, Deepseek, Claude, Gemini and more.

Published on
August 8, 2025
Nightfall Demo: Detect & Remediate Data Exposure in SaaS
Learn how Nightfall detects and remediates sensitive data exposure in SaaS apps like Slack, Google Workspace, Atlassian, Salesforce, Microsoft 365 and more.

Published on
August 8, 2025
Nightfall Demo: Manage Sharing Permissions Settings in SaaS Apps
Manage external sharing risks in SaaS apps like Google Drive and Slack with real-time alerts, automated remediation, and data lineage.

Published on
August 8, 2025
Nightfall Demo: DLP for Gmail
Native Gmail integration scans emails inline and allows users to set up custom policies to block, quarantine, redact, and encrypt emails for a full range of email security options.

Published on
August 8, 2025
Nightfall Demo: Secure Data When Using Gen AI Tools & Chatbots
Nightfall’s endpoint agent and browser plugin keeps your data safe across AI apps. See the power of gaining full visibility and context through data lineage.

Published on
August 8, 2025
Nightfall Demo: Protecting Data in Endpoints and Browsers with AI
Nightfall prevents data exfiltration for endpoints and browsers with AI-native DLP that’s lightweight and seamless to integrate into all your systems.

Published on
August 7, 2025
Eclipse - Nyx Copilot
Meet Nyx, Nightfall’s new agentic AI copilot for DLP. Nyx works like a teammate: she understands context, acts safely, and simplifies complex workflows.
.png)
Published on
August 7, 2025
Eclipse - A Unique Approach to Endpoint DLP
See Nightfall in action in this live demonstration of our latest data lineage capabilities and comprehensive coverage across all major exfiltration vectors.

Published on
August 7, 2025
Eclipse - Comprehensive AI-Powered DLP for Microsoft 365
See how to protect data across Microsoft Sharepoint and Exchange with Nightfall’s comprehensive M365 DLP featuring advanced AI detection and smart remediation.

Published on
August 7, 2025
Eclipse - Opening Keynote: Key Product Announcements
Nightfall co-founder and CEO Rohan Sathe shares an exclusive first look at Nightfall's latest breakthrough innovations in AI-powered DLP.

Published on
August 7, 2025
Eclipse - A Fireside Chat with Rohan Sathe & Enrique Salem
Nightfall co-founder Rohan Sathe and Enrique Salem, Partner at BCV, discuss the future of AI-powered data loss prevention from builder and investor perspectives.

Published on
August 7, 2025
Eclipse - Secure AI Adoption: Preventing Leakage in Shadow AI Applications
Learn how to implement visibility and controls that prevent sensitive data leakage to AI applications without blocking productivity with Nightfall DLP.

Published on
July 1, 2024
3 Ways to Prevent Data Exfiltration in your SaaS Apps
Data exfiltration poses a significant threat to organizations across all industries. With cybercriminals using increasingly sophisticated methods to illicitly obtain sensitive information, IT and security teams face the daunting task of protecting their digital assets against both internal and external threats. This webinar will provide your team some practical strategies to enhance your company's defenses against data exfiltration.

Published on
May 20, 2024
Protect Your Email From Sensitive Data Loss and Data Exfiltration
Email remains a critical channel for business communication and also remains a prime exfiltration and attack vector. Traditional Secure Email Gateways (SEGs) and rules-based DLP solutions are proving inadequate against data loss, exfiltration, sophisticated attacks and the complexities of modern cloud environments. Whether your organization relies on Gmail or Exchange or a hybrid email environment, Nightfall AI can protect your email against data loss and exfiltration with a comprehensive, flexible, and efficient approach to protecting your email across platforms.

Published on
December 6, 2023
Building Security at an Enterprise Scale
Nightfall for Notion DLP is purpose-built to pinpoint sensitive data across Notion workspaces. Whether you’re using Notion as an internal wiki, a note-taking app, or something more, Nightfall’s AI-powered detectors will identify and remediate high-priority risks to ensure that your business stays continuously secure and compliant as you scale.

Published on
November 28, 2023
Next-Gen Secrets Detection for the Age of AI
All employees have a part to play in keeping company secrets safe—however, developers have an outsized role due to their privileged access to sensitive databases, production systems, and source code. With these unique challenges in mind, Nightfall partnered with Snyk to offer AI-powered secrets scanning for developers working in every stage of the code-to-cloud lifecycle.

Published on
August 1, 2023
ChatGPT and Gen AI: How to Stay Secure and Compliant
Generative AI is exploding, allowing companies to do more with less. It is, however, also exposing companies to more data security risks than ever before. In our upcoming fireside chat, we'll join Enrique Salem, former CEO of Symantec, and Isaac Madan, CEO of Nightfall, to discuss the biggest security risks of Gen AI, as well as strategies you need to stay compliant without impacting employee innovation. By the end of the chat, you'll be armed with the tools you need to safely use ChatGPT and other Gen AI tools across your business. See you there!

Published on
July 10, 2023
How Security and Compliance Can Help Unlock Enterprise Customers
Security is of paramount importance for organizations trying to shorten their sales cycles and unlock enterprise clients. Learn how to use security as a differentiator in today’s challenging macroeconomic climate.

Published on
June 14, 2022
Build Continuous Security & Compliance into Your SaaS Environments
As recent trends, like supply chain attacks and cloud data leaks have made clear, continuous security and continuous data compliance must be embedded into the application, no matter where it is deployed, and who is accessing it.

Published on
June 8, 2021
Learn How to Protect Codebases from Secrets Exfiltration
Listen to Nightfall’s CTO, Rohan Sathe, and product specialist, Michael Osakwe, to learn about the increased exfiltration risks posed by code repositories. Learn how threat actors are incorporating targets like GitHub into their attacks, why this has become more common, and best practices to reduce your attack surface.

Published on
June 14, 2022
Enhance Data Governance & Intelligence across SaaS Systems
Enterprise legal, compliance, and governance teams struggle to detect, manage, govern, and protect information in near real time. Similarly, litigation, HR and investigation teams struggle with data intelligence on information they have collected from cloud applications like Slack and Google Workspace.

Published on
November 22, 2021
Learn How Bluecore Maintains Data Security on Slack with Nightfall
SaaS applications like Slack are challenging environments for enforcing data security policies. This is especially true for innovative, high-growth companies that have embraced a cloud-first philosophy.

Published on
April 28, 2021
Data Classification & Protection with the Nightfall Developer Platform
A myriad of organizations rely on Nightfall, the industry’s first cloud-native data loss prevention (DLP) solution, to implement DLP into essential cloud applications like Slack, GitHub, and Google Drive.

Published on
August 24, 2020
HIPAA Compliance Requirements & Best Practices for Slack
It's important that HIPAA covered entities interested in Slack understand what's needed to ensure they remain compliant while using the platform.

Published on
April 8, 2020
How to Discover & Protect Sensitive Data in Slack
Collaborative SaaS applications like Slack create environments where data policy and security best practices are difficult to maintain or enforce without an excessive time or resource commitment.

Published on
March 2, 2021
How to Identify & Protect Sensitive Data in AWS
Some of the biggest data leaks in history have occurred due to problems with Amazon Web Services (AWS S3), like permissions misconfigurations, secrets mismanagement, improper security configurations, or maintaining a poor visibility environment.

Published on
March 2, 2021
Securing Best of Breed SaaS Applications in 2021
The explosive growth of SaaS collaboration tools and other cloud-based platforms makes it paramount that organizations understand how to secure data in the cloud

Published on
March 2, 2021
Discover Secrets Leaks in Code Repos with Nightfall for GitHub
Git-based repositories can create environments where secrets & credentials are exposed without notice, especially in environments with lots of contributors and few guidelines regarding best practices for handling credentials or environments with external collaborators who might not be familiar with best practices

Published on
July 8, 2025
Protected Health Information (PHI) detector for digital healthcare datasheet
Healthcare organizations require an effective way to scale HIPAA compliance enforcement across their cloud applications without excessive time and resource commitment. This requires a high-accuracy solution capable of parsing context to identify PHI violations as they are defined by HIPAA

Published on
July 8, 2025
Nightfall Advanced Secrets Detection Datasheet
Exposure of secrets like API keys is a common problem that can lead to privilege escalation of security incidents if accessed by malicious actors. Addressing this problem requires a solution tuned to detect secrets in any format, wherever they are.

Published on
July 8, 2025
PCI Compliance Checklist for Modern Organizations
This checklist highlights core aspects of PCI compliance and security standards, as well as how to implement them.

Published on
July 8, 2025
Cloud Security Policy Template
Protecting your data in the cloud starts with developing a cloud security policy to govern user access, meet compliance standards, secure data in use, and maintain defenses against cyber threats.

Published on
July 8, 2025
Guide to Data Loss Prevention (DLP) for Jira
Data loss prevention (DLP) is an important part of data security and compliance in the cloud, especially for organizations using SaaS applications that store high volumes of data. Companies turn to DLP solutions to discover, classify, and protect their sensitive data in environments like Jira, and maintain compliance with regimes like GDPR, CCPA, PCI, and more.

Published on
July 8, 2025
Guide to Data Loss Prevention (DLP) for Github
Learn how to detect the leakage of secrets, credentials, and other sensitive data across your code repositories with this brief guide.

Published on
July 8, 2025
Guide to HIPAA Compliance on Slack
Data loss prevention (DLP) is an important part of data security and compliance in the cloud, especially for organizations regulated by HIPAA. Furthermore, healthcare teams using Slack must follow specific guidelines laid out in Slack’s Business Associate Agreement (BAA).

Published on
July 8, 2025
6 Steps to Protect Google Drive with Data Loss Protection
Google Drive is core to enabling collaboration and access to business-critical files, but it is difficult to audit which files within Google Drive have sensitive information and who has access to them.

Published on
July 8, 2025
The 2023 Security Playbook for Remote-First Organizations
Learn how to more securely manage your remote workforce to become a true remote-first organization.

Published on
July 8, 2025
Guide to Data Loss Prevention (DLP) in Google Drive
Data loss prevention (DLP) is an important part of data security and compliance in the cloud, especially for organizations using SaaS applications that store high volumes of data. Companies turn to DLP solutions to discover, classify, and protect their sensitive data in environments like Google Drive, and maintain compliance with regimes like GDPR, CCPA, PCI, and more.

Published on
July 8, 2025
Data Security with the Nightfall Developer Platform
As a result of growing data breaches governments across the world are beginning to implement compliance regimes which require organizations to understand the quantity and nature of that data they’re ingesting. The Nightfall developer platform is designed to help organizations accomplish this with APIs that allow developers to stream data to our machine learning detectors for classification.

Published on
July 8, 2025
Guide to Data Loss Prevention (DLP) for Confluence
Learn how to detect the leakage of secrets and other business-critical data within Atlassian Confluence

Published on
July 8, 2025
Guide To HIPAA Compliance for SaaS Applications
SaaS applications enable healthcare organizations to leverage digital transformation to improve healthcare outcomes and change lives, but ensuring your organization remains compliant while adopting cloud applications can prove challanging.

Published on
July 8, 2025
The Business Case for Cloud Data Protection
As organizations continue to rapidly adopt SaaS and cloud infrastructure, IT and security teams are becoming stretched. The expanding universe of business-critical cloud applications creates increased risk for the exposure of sensitive data like PII, PHI, as well as secrets and credentials. Cloud data protection is essential to ensuring employees follow best practices for handling sensitive data and that systems are configured in a manner that prevents unauthorized access.

Published on
July 8, 2025
Guide To Data Loss Prevention (DLP) for Salesforce
Learn how to discover and prevent the leakage of customer information and other business-critical data within Salesforce

Published on
July 8, 2025
HIPAA Security Rule Implementation Specification Matrix
In order to fulfill the HIPAA Security Rule, covered entities and business associates must evaluate the implementation specifications or requirements listed under each Security Rule Safeguard in order to determine how best satisfy each. We’ve built out a matrix to explain each individual HIPAA Security Rule requirement in plain English.

Published on
July 8, 2025
The Ultimate HIPAA Security & Compliance FAQ
HIPAA compliance is a complex topic. That’s why we’ve complied the most frequently asked questions with detailed answers to help guide you through the compliance process.

Published on
July 8, 2025
Guide to Data Loss Prevention (DLP) for Slack
Data loss prevention (DLP) is an important part of data security and compliance in the cloud. Companies turn to DLP solutions to discover, classify, and protect their sensitive data in collaborative environments like Slack, and maintain compliance with regimes like HIPAA, GDPR, CCPA, PCI, and more.
More stories
.png)
Data Exfiltration Prevention: 5 Best Practices for Modern Security Teams
Most data loss today bypasses traditional DLP entirely. Sensitive data now moves through AI tools, personal cloud accounts, privacy-first browsers, and Git repositories. Often without ever touching the controls security teams rely on.
.png)
Data Exfiltration Prevention: 5 Best Practices for Modern Security Teams
Most data loss today bypasses traditional DLP entirely. Sensitive data now moves through AI tools, personal cloud accounts, privacy-first browsers, and Git repositories. Often without ever touching the controls security teams rely on.

Do You Use These Top SaaS Apps? Here’s what you need to know about Data Sprawl
Nightfall’s recent “State of Secrets” report uncovered that collaboration, communication, and IT service tools have the highest risk of data exposure, particularly in industry-leading SaaS apps like Slack and GitHub.

Protected Health Information (PHI) detector for digital healthcare datasheet
Healthcare organizations require an effective way to scale HIPAA compliance enforcement across their cloud applications without excessive time and resource commitment. This requires a high-accuracy solution capable of parsing context to identify PHI violations as they are defined by HIPAA

Guide to HIPAA Compliance on Slack
Data loss prevention (DLP) is an important part of data security and compliance in the cloud, especially for organizations regulated by HIPAA. Furthermore, healthcare teams using Slack must follow specific guidelines laid out in Slack’s Business Associate Agreement (BAA).
.webp)
Guide to Data Loss Prevention (DLP) for Jira
Data loss prevention (DLP) is an important part of data security and compliance in the cloud, especially for organizations using SaaS applications that store high volumes of data. Companies turn to DLP solutions to discover, classify, and protect their sensitive data in environments like Jira, and maintain compliance with regimes like GDPR, CCPA, PCI, and more.

Guide to Data Loss Prevention (DLP) in Google Drive
Data loss prevention (DLP) is an important part of data security and compliance in the cloud, especially for organizations using SaaS applications that store high volumes of data. Companies turn to DLP solutions to discover, classify, and protect their sensitive data in environments like Google Drive, and maintain compliance with regimes like GDPR, CCPA, PCI, and more.

Data Security with the Nightfall Developer Platform
As a result of growing data breaches governments across the world are beginning to implement compliance regimes which require organizations to understand the quantity and nature of that data they’re ingesting. The Nightfall developer platform is designed to help organizations accomplish this with APIs that allow developers to stream data to our machine learning detectors for classification.

The Business Case for Cloud Data Protection
As organizations continue to rapidly adopt SaaS and cloud infrastructure, IT and security teams are becoming stretched. The expanding universe of business-critical cloud applications creates increased risk for the exposure of sensitive data like PII, PHI, as well as secrets and credentials. Cloud data protection is essential to ensuring employees follow best practices for handling sensitive data and that systems are configured in a manner that prevents unauthorized access.

Do You Use These Top SaaS Apps? Here’s what you need to know about Data Sprawl
Nightfall’s recent “State of Secrets” report uncovered that collaboration, communication, and IT service tools have the highest risk of data exposure, particularly in industry-leading SaaS apps like Slack and GitHub.


3 Ways to Prevent Data Exfiltration in your SaaS Apps
Data exfiltration poses a significant threat to organizations across all industries. With cybercriminals using increasingly sophisticated methods to illicitly obtain sensitive information, IT and security teams face the daunting task of protecting their digital assets against both internal and external threats. This webinar will provide your team some practical strategies to enhance your company's defenses against data exfiltration.

Protect Your Email From Sensitive Data Loss and Data Exfiltration
Email remains a critical channel for business communication and also remains a prime exfiltration and attack vector. Traditional Secure Email Gateways (SEGs) and rules-based DLP solutions are proving inadequate against data loss, exfiltration, sophisticated attacks and the complexities of modern cloud environments. Whether your organization relies on Gmail or Exchange or a hybrid email environment, Nightfall AI can protect your email against data loss and exfiltration with a comprehensive, flexible, and efficient approach to protecting your email across platforms.

Building Security at an Enterprise Scale
Nightfall for Notion DLP is purpose-built to pinpoint sensitive data across Notion workspaces. Whether you’re using Notion as an internal wiki, a note-taking app, or something more, Nightfall’s AI-powered detectors will identify and remediate high-priority risks to ensure that your business stays continuously secure and compliant as you scale.

Next-Gen Secrets Detection for the Age of AI
All employees have a part to play in keeping company secrets safe—however, developers have an outsized role due to their privileged access to sensitive databases, production systems, and source code. With these unique challenges in mind, Nightfall partnered with Snyk to offer AI-powered secrets scanning for developers working in every stage of the code-to-cloud lifecycle.

ChatGPT and Gen AI: How to Stay Secure and Compliant
Generative AI is exploding, allowing companies to do more with less. It is, however, also exposing companies to more data security risks than ever before. In our upcoming fireside chat, we'll join Enrique Salem, former CEO of Symantec, and Isaac Madan, CEO of Nightfall, to discuss the biggest security risks of Gen AI, as well as strategies you need to stay compliant without impacting employee innovation. By the end of the chat, you'll be armed with the tools you need to safely use ChatGPT and other Gen AI tools across your business. See you there!

Enhance Data Governance & Intelligence across SaaS Systems
Enterprise legal, compliance, and governance teams struggle to detect, manage, govern, and protect information in near real time. Similarly, litigation, HR and investigation teams struggle with data intelligence on information they have collected from cloud applications like Slack and Google Workspace.

Build Continuous Security & Compliance into Your SaaS Environments
As recent trends, like supply chain attacks and cloud data leaks have made clear, continuous security and continuous data compliance must be embedded into the application, no matter where it is deployed, and who is accessing it.

Learn How to Protect Codebases from Secrets Exfiltration
Listen to Nightfall’s CTO, Rohan Sathe, and product specialist, Michael Osakwe, to learn about the increased exfiltration risks posed by code repositories. Learn how threat actors are incorporating targets like GitHub into their attacks, why this has become more common, and best practices to reduce your attack surface.

Discover Secrets Leaks in Code Repos with Nightfall for GitHub
Git-based repositories can create environments where secrets & credentials are exposed without notice, especially in environments with lots of contributors and few guidelines regarding best practices for handling credentials or environments with external collaborators who might not be familiar with best practices

Protected Health Information (PHI) detector for digital healthcare datasheet
Healthcare organizations require an effective way to scale HIPAA compliance enforcement across their cloud applications without excessive time and resource commitment. This requires a high-accuracy solution capable of parsing context to identify PHI violations as they are defined by HIPAA

Guide to HIPAA Compliance on Slack
Data loss prevention (DLP) is an important part of data security and compliance in the cloud, especially for organizations regulated by HIPAA. Furthermore, healthcare teams using Slack must follow specific guidelines laid out in Slack’s Business Associate Agreement (BAA).
.webp)
Guide to Data Loss Prevention (DLP) for Jira
Data loss prevention (DLP) is an important part of data security and compliance in the cloud, especially for organizations using SaaS applications that store high volumes of data. Companies turn to DLP solutions to discover, classify, and protect their sensitive data in environments like Jira, and maintain compliance with regimes like GDPR, CCPA, PCI, and more.

Guide to Data Loss Prevention (DLP) in Google Drive
Data loss prevention (DLP) is an important part of data security and compliance in the cloud, especially for organizations using SaaS applications that store high volumes of data. Companies turn to DLP solutions to discover, classify, and protect their sensitive data in environments like Google Drive, and maintain compliance with regimes like GDPR, CCPA, PCI, and more.

Data Security with the Nightfall Developer Platform
As a result of growing data breaches governments across the world are beginning to implement compliance regimes which require organizations to understand the quantity and nature of that data they’re ingesting. The Nightfall developer platform is designed to help organizations accomplish this with APIs that allow developers to stream data to our machine learning detectors for classification.

The Business Case for Cloud Data Protection
As organizations continue to rapidly adopt SaaS and cloud infrastructure, IT and security teams are becoming stretched. The expanding universe of business-critical cloud applications creates increased risk for the exposure of sensitive data like PII, PHI, as well as secrets and credentials. Cloud data protection is essential to ensuring employees follow best practices for handling sensitive data and that systems are configured in a manner that prevents unauthorized access.

HIPAA Security Rule Implementation Specification Matrix
In order to fulfill the HIPAA Security Rule, covered entities and business associates must evaluate the implementation specifications or requirements listed under each Security Rule Safeguard in order to determine how best satisfy each. We’ve built out a matrix to explain each individual HIPAA Security Rule requirement in plain English.

Guide to Data Loss Prevention (DLP) for Slack
Data loss prevention (DLP) is an important part of data security and compliance in the cloud. Companies turn to DLP solutions to discover, classify, and protect their sensitive data in collaborative environments like Slack, and maintain compliance with regimes like HIPAA, GDPR, CCPA, PCI, and more.
Popular Resources
















.webp)

.webp)

