
AI-native data exfiltration prevention for endpoints, SaaS and AI apps
Nightfall prevents sensitive data from leaving your organization across endpoints, SaaS, and AI tools. Trace data flows, block risky actions, and empower employees through real-time, automated coaching.
Endpoint DLP and insider risk management (IRM) tools fail in the modern workplace.
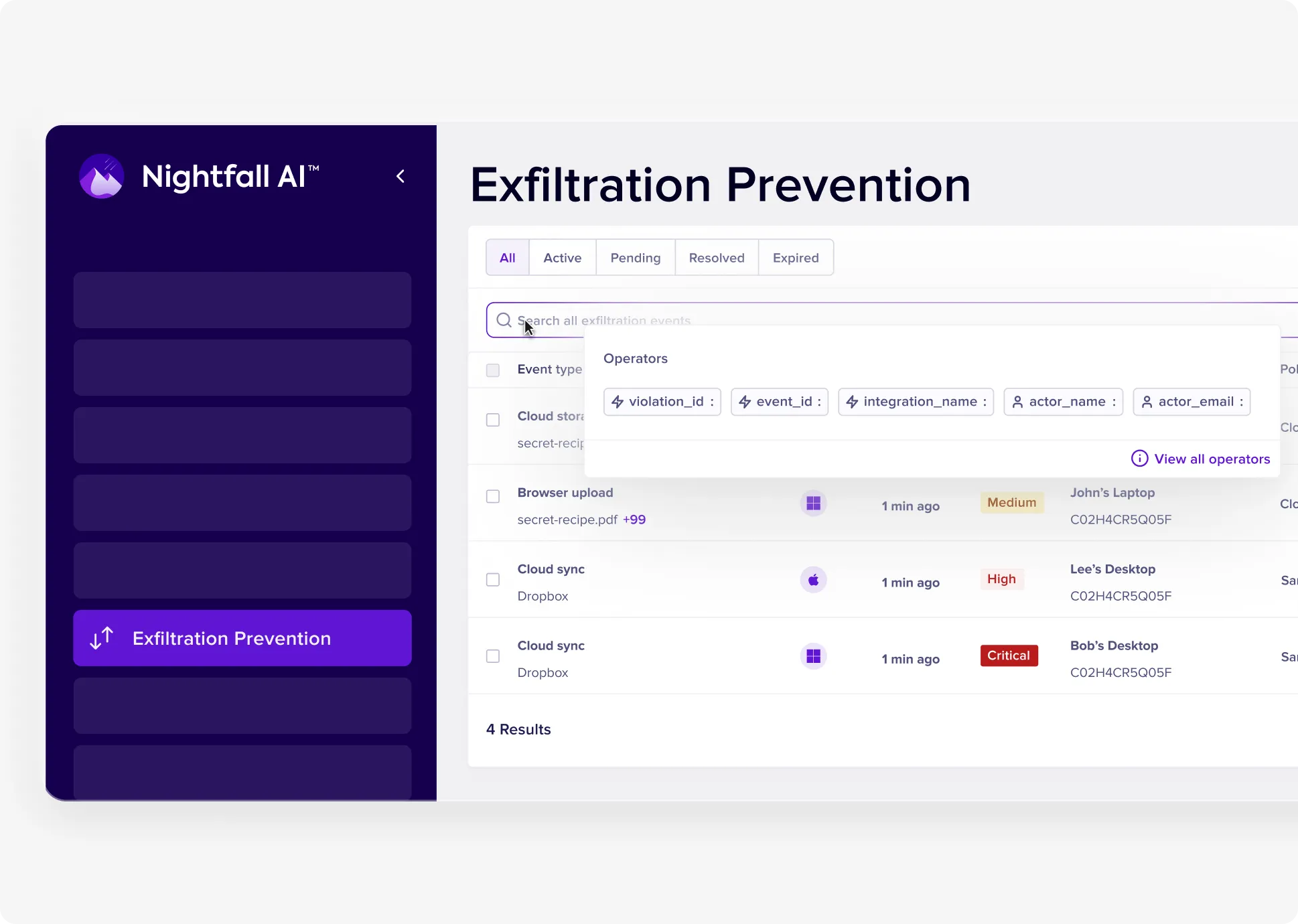
Prevent Data Exfiltration Across Every Channel
Sensitive data leaves through endpoints, personal cloud uploads, USB transfers, and AI tools. Nightfall monitors all vectors with lightweight agents and browser plugins—blocking risky behavior in real time and capturing full evidence for investigations.

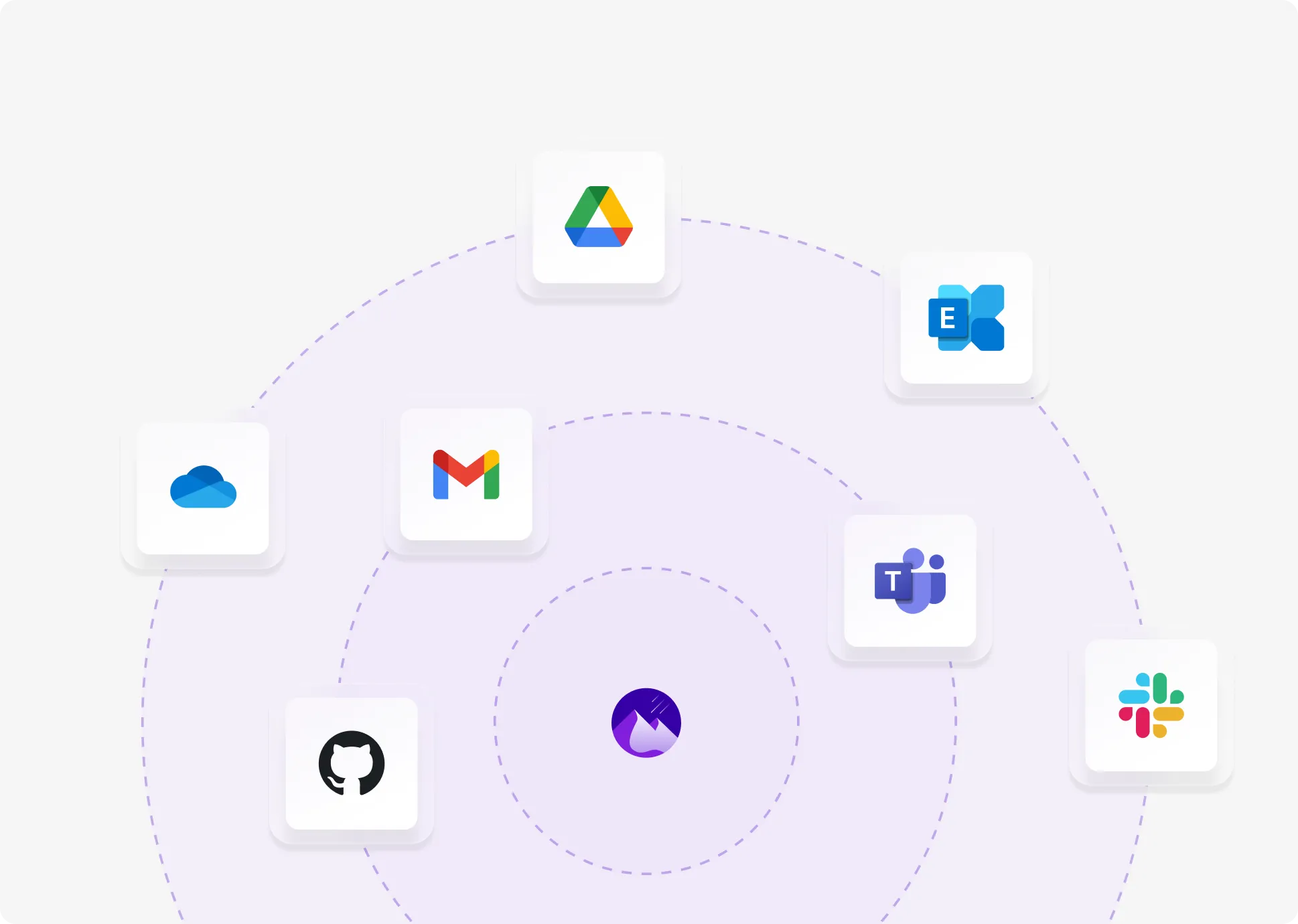
Eliminate Blind Spots in AI Apps
Legacy DLP can’t see what employees paste into ChatGPT or upload to generative AI platforms. Nightfall captures prompts, copy/paste, and file uploads—automatically classifying and blocking PII, financial data, and source code before it leaves your control.

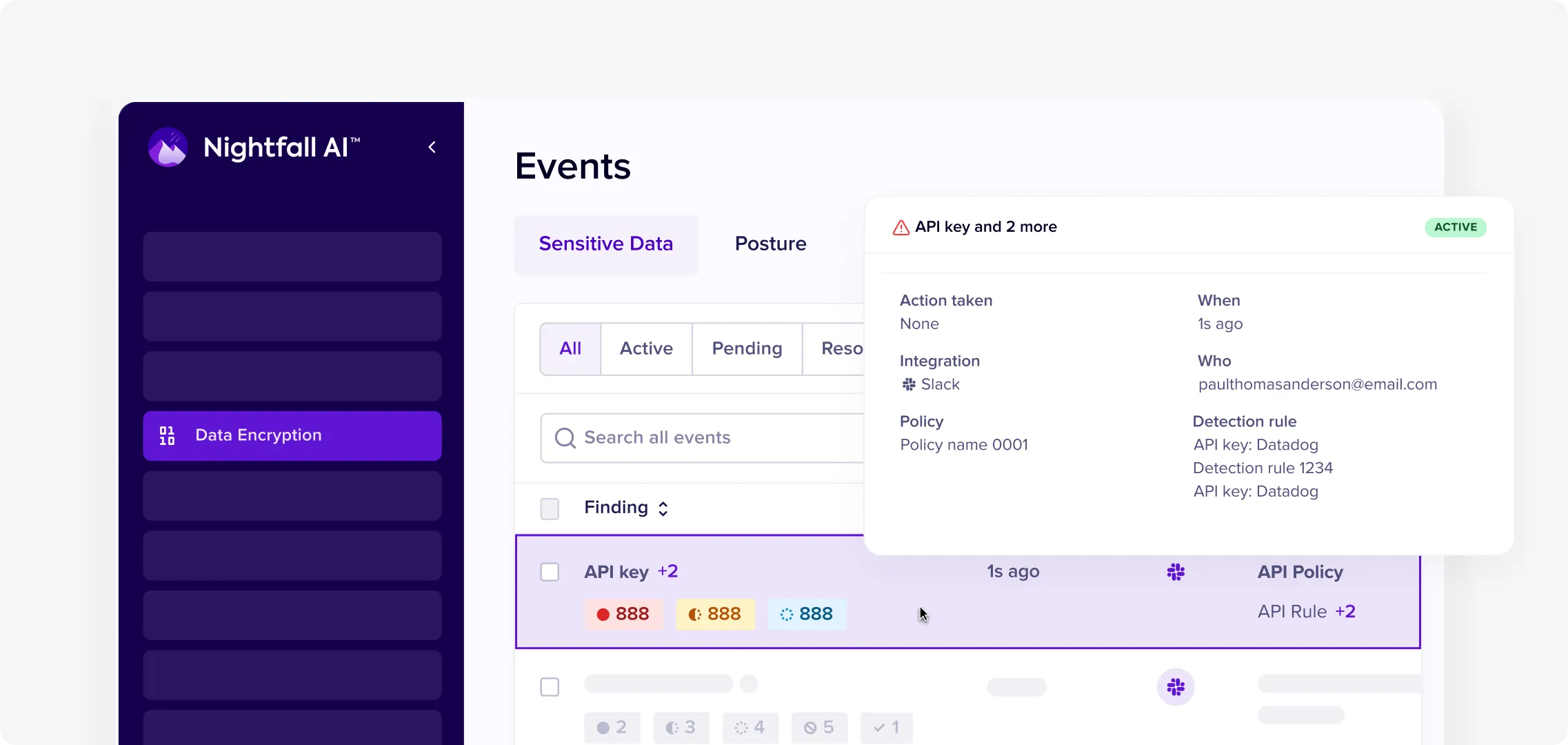
Accelerate Investigations with Complete Context
When incidents occur, Nightfall provides instant clarity. Session replay shows user actions, file preview reveals exposed content, and data lineage tracks document origin. No more piecing together evidence from incomplete logs.
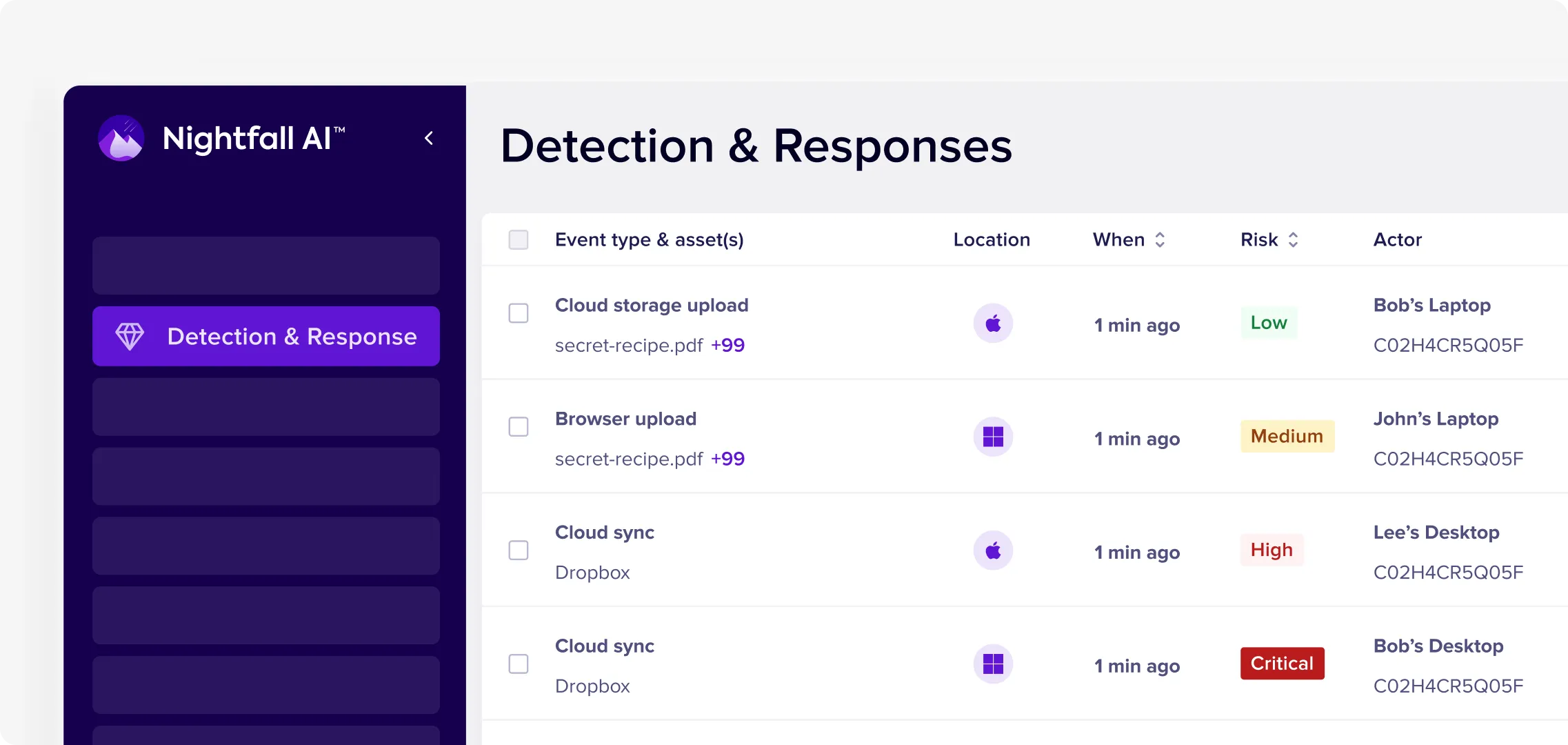
Focus Security on Real IP Threats
AI-powered classification distinguishes legitimate work from actual exfiltration attempts. Automatic policy tuning based on data sensitivity and user behavior keeps intellectual property secure while allowing businesses to move fast.
The Nightfall Impact
Organizations that switch from legacy DLP to Nightfall consistently report

Time to Value
Deploy across your entire ecosystem in under a day versus the 6+ months with legacy alternatives.
.webp)
Operational Efficiency
90% reduction in false positives. Stop wasting your security team's limited resources on alerts that go nowhere.

Coverage
100% visibility across exfiltration channels. Eliminate the gaps between point solutions where your most sensitive data was escaping.

Compliance Outcomes
Evidence-ready reporting streamlines SOC 2, PCI DSS, and HIPAA audits.

Context-Aware, AI-Powered Classification
Automatically identify customer records, financial data, source code, and confidential documents. Detect obfuscated content, images, and screenshots that legacy pattern-matching DLP misses.
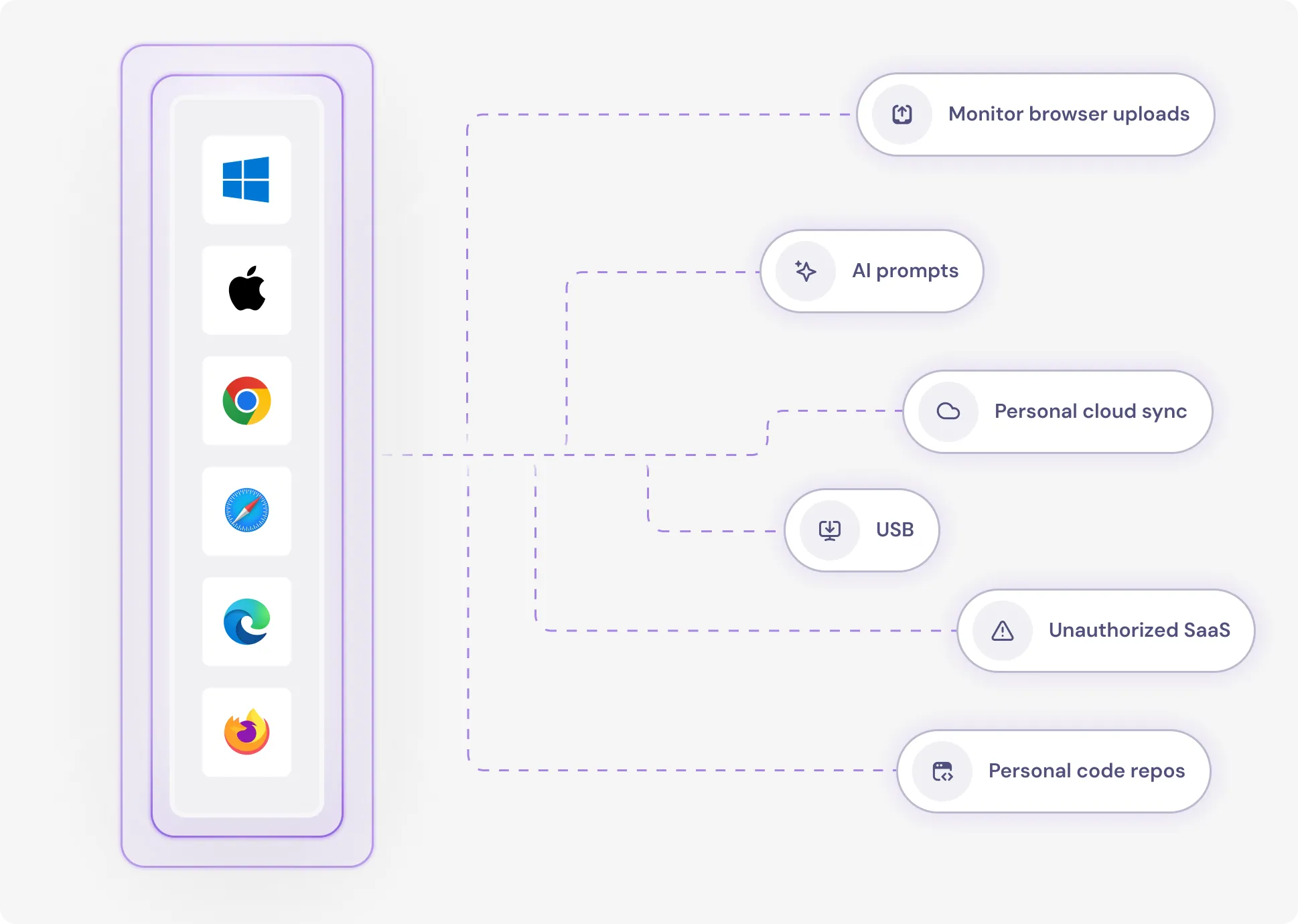
Coverage Across All Exfiltration Vectors
Monitor browser uploads, AI prompts, personal cloud sync, USB, unauthorized SaaS, and personal code repos. Works across macOS, Windows, Chrome, Firefox, Safari, and Edge—no network changes required.
Forensic Session Replay
Screen recordings capture exactly how data was accessed, copied, and transferred—providing clear evidence for compliance reviews, insider threat investigations, and employee coaching.
AI-Powered Data Lineage
Trace sensitive documents from corporate origin to external destination. See when files are downloaded, renamed, compressed, and exfiltrated—ensuring audit-ready visibility for every flow.
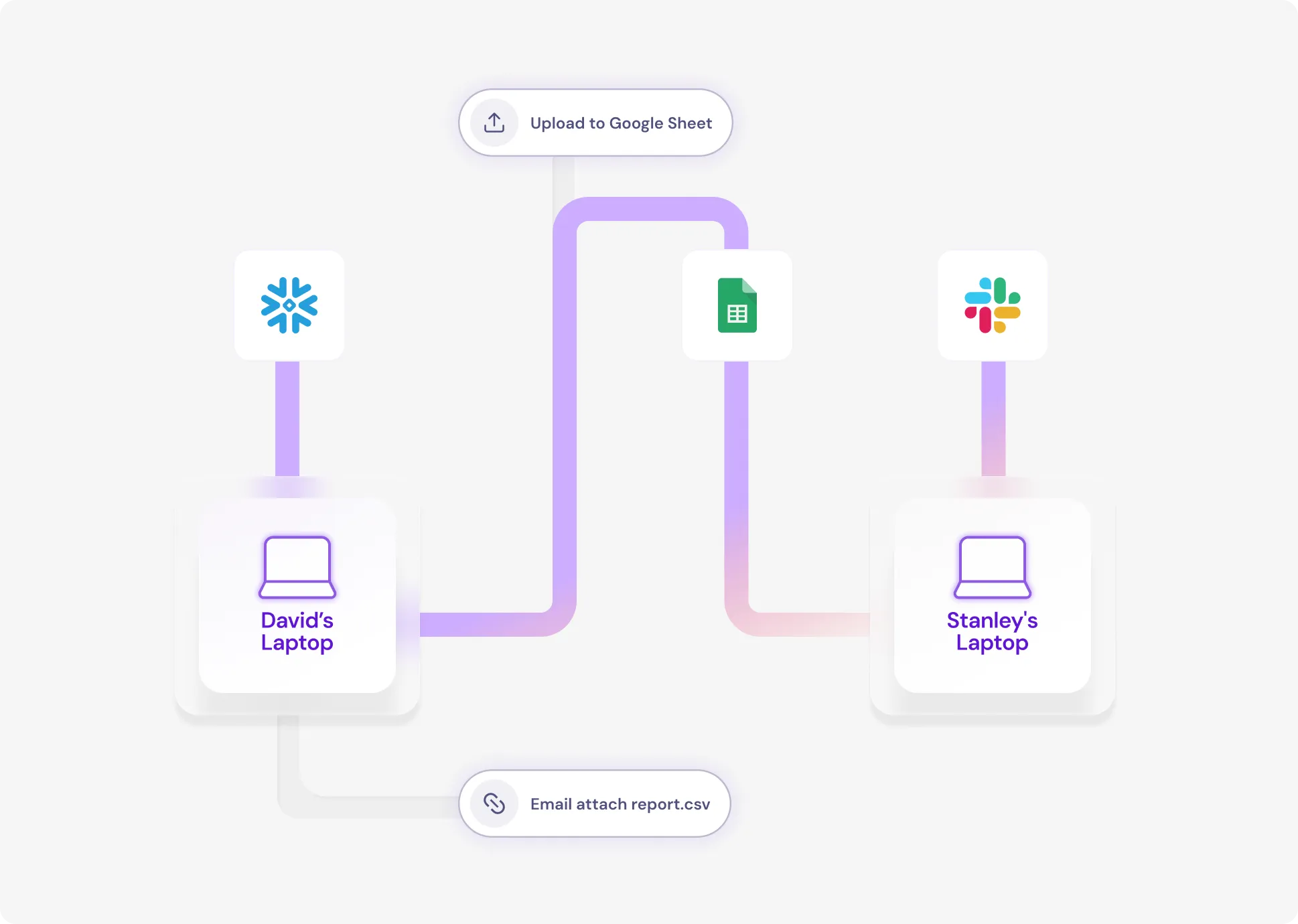
Source Code & IP Protection
Specialized detection for code repositories, secrets, and development artifacts. Block uploads to unauthorized Git repos, prevent code snippets in AI prompts, and track IP across engineering workflows.
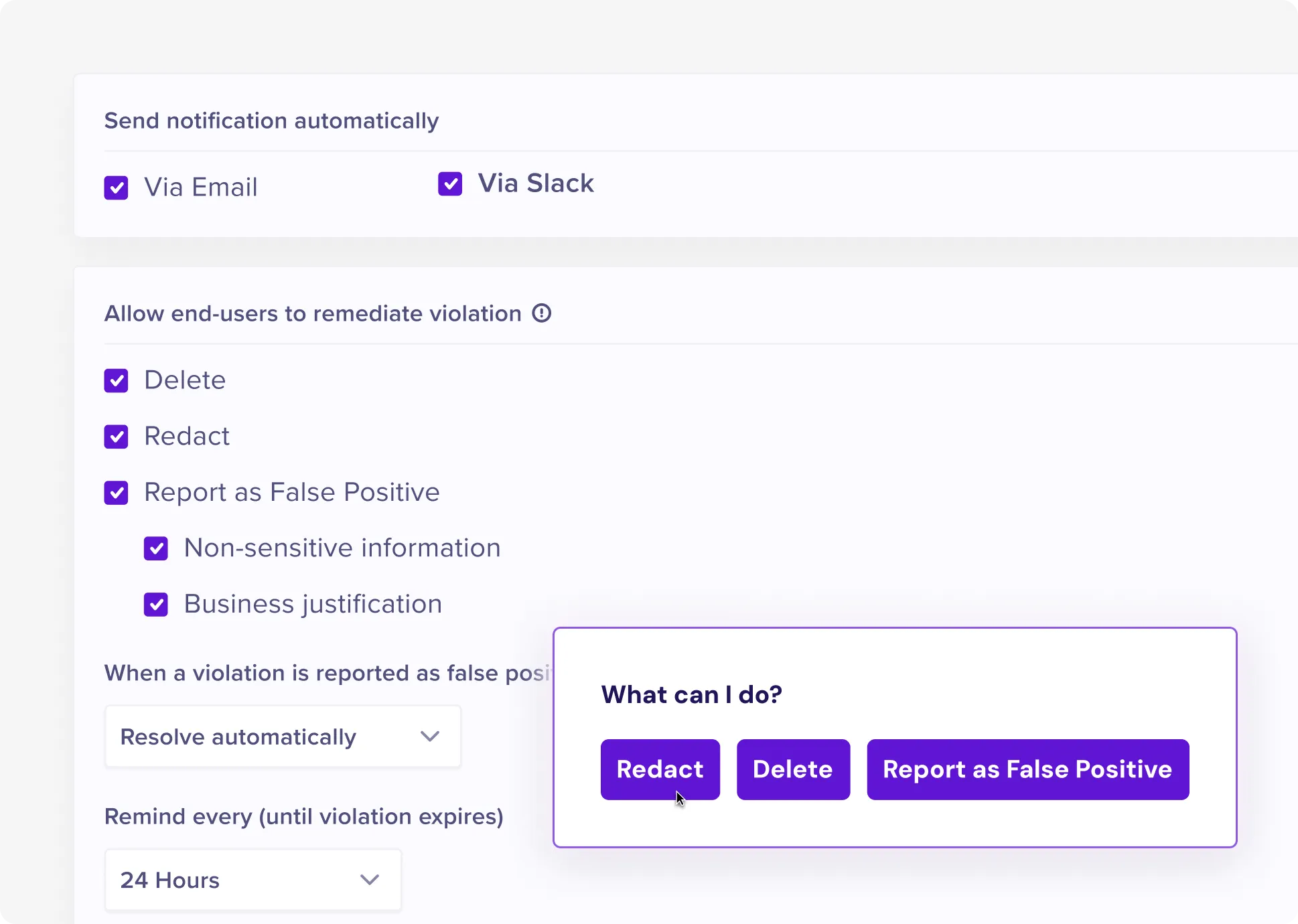
Real-Time Employee Coaching
Turn violations into teachable moments with contextual notifications on endpoint, Slack, Teams, or Email. Build long-term security awareness while reducing adversarial enforcement.
Nyx AI Copilot for Autonomous DLP
The industry’s first autonomous DLP copilot. Nyx investigates incidents, tunes policies, and surfaces risk insights—delivering real-time prevention across uploads, sync, copy/paste, USB, and email transfers.
Case studies
Loved by innovative security teams
95%
precision
10x
lower total cost of ownership
80%
self-resolution


Schedule a live demo
Tell us a little about yourself and we'll connect you with a Nightfall expert who can share more about the product and answer any questions you have.
Not yet ready for a demo? Read our latest e-book, Protecting Sensitive Data from Shadow AI.

%201.webp)




%201.webp)
%201.webp)
%201.webp)






.webp)


